Configuring NSX-T for IDS/IPS Event Forwarding to a Syslog Server
Article ID: 377739
Updated On:
Products
Issue/Introduction
IDS/IPS events will not automatically generate logs on the ESXi host thus the events will not be sent to an event syslog server. This document guides on how to enable and configure NSX to forward IDS/IPS events to a syslog server.
Environment
NSX-T 3.x and above.
vDefend Firewall
Cause
The lack of IDS/IPS logs by default is intentional
Resolution
The NSX documentation gives you a hint on how to forward the events.
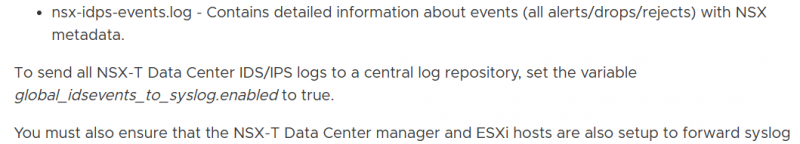
The NSX IDS/IPS and Distributed Firewall (DFW) logs and events are generated on the ESXi hosts. The IDS/IPS log files are stored in the directory /var/run/log/nsx-idps. By default, IDS/IPS event logging to syslog is disabled.
Follow these steps for NSX 3.1.x to enable IDS/IPS logging:
-
Check Current Configuration: Perform a GET request to the NSX Manager API at /api/v1/global-configs/IdsGlobalConfig using a tool like Postman. This will show the current configuration, including whether global_idsevents_to_syslog_enabled is set to false.
GET https://<Manager-IP>/api/v1/global-configs/IdsGlobalConfig -
Modify the Configuration: Copy the current configuration details, including the top two lines and the _revision line, into a new JSON file. Update the global_idsevents_to_syslog_enabled setting to true:
{
"global_idsevents_to_syslog_enabled": true,
"resource_type": "IdsGlobalConfig",
"_revision": 2
} -
Update Configuration: Use a PUT request to the same API endpoint to apply the changes.
PUT https://<Manager-IP>/api/v1/global-configs/IdsGlobalConfig -
Verification: Trigger an IDS/IPS event. The events should now appear in the /var/run/log/nsx-idps/nsx-idps-events.log file on the ESXi host.
-
After enabling syslog on the Host, these IDS/IPS events will be automatically forwarded to any syslog server like Log Insight.
Follow these steps for NSX 3.2.x and later to enable IDS/IPS logging:
1. Check Current IDS/IPS Configuration: Run the following API request to check the current IDS/IPS settings:
GET https://<Manager-IP>/api/v1/infra/settings/firewall/security/intrusion-services/ {
"auto_update": true,
"ids_ever_enabled": true,
"ids_events_to_syslog": false,
"oversubscription": "BYPASSED",
"resource_type": "IdsSettings",
"id": "intrusion-services",
"display_name": "intrusion-services",
"_revision": 5
} 2. Enable IDS/IPS Syslog: To enable sending IDS/IPS logs to a central repository, set the ids_events_to_syslog parameter to true using the following API request:
PATCH https://<Manager-IP>/api/v1/infra/settings/firewall/security/intrusion-services/{
"auto_update": true,
"ids_ever_enabled": true,
"ids_events_to_syslog": true,
"oversubscription": "BYPASSED",
"resource_type": "IdsSettings",
"id": "intrusion-services",
"display_name": "intrusion-services"
}
4. Verification: Trigger an IDS/IPS event. The events should now appear in the /var/run/log/nsx-idps/nsx-idps-events.log file on the ESXi host.
5. After enabling syslog on the Host, these IDS/IPS events will be automatically forwarded to any syslog server like Log Insight.
