HCX for VMC - Protecting HCX Cloud Manager for Internet Access
Article ID: 336974
Updated On:
Products
VMware HCX
VMware Cloud on AWS
VMware Cloud on Dell EMC
Issue/Introduction
For HCX deployments in an SDDC in VMware Cloud on AWS or VMware Cloud on Dell EMC, it is highly recommended to restrict access to the Cloud Manager when using internet connectivity. Private access through DX or VPN is expected to be intrinsically secured.
Using the Management Gateway Firewall to limit the communication protocols that can be used and configure a specific set of source IP address, it will minimize the security risk to HCX and the SDDC.
Using the Management Gateway Firewall to limit the communication protocols that can be used and configure a specific set of source IP address, it will minimize the security risk to HCX and the SDDC.
Resolution
The following procedure can be used to setup the basic Firewall rules:
IMPORTANT: If these rules are created after the Site Pairings were established, verify those remain UP after the rules are applied, to ensure there is no impact due to misconfigurations.
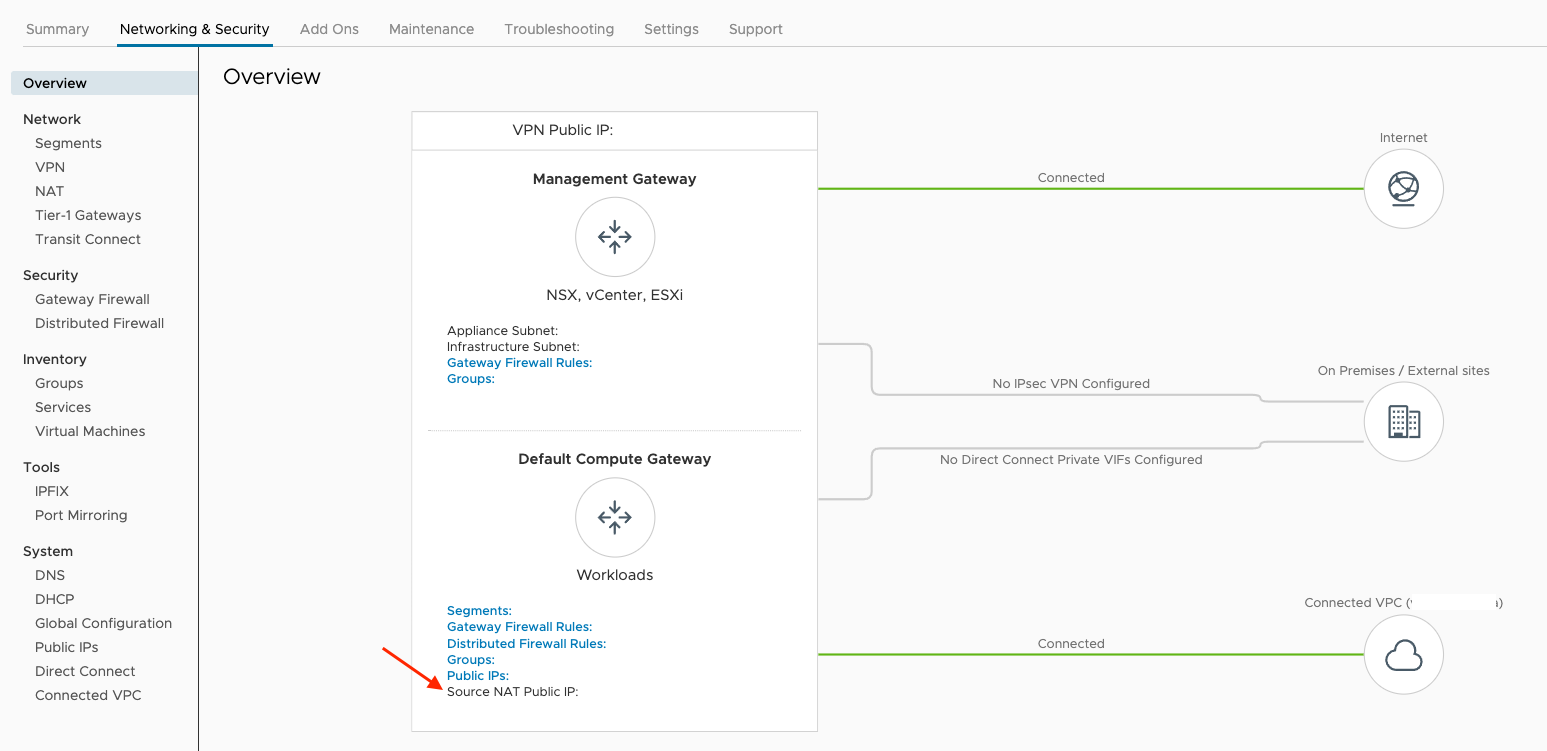
- At the VMC console, navigate to the "Networking & Security" tab.
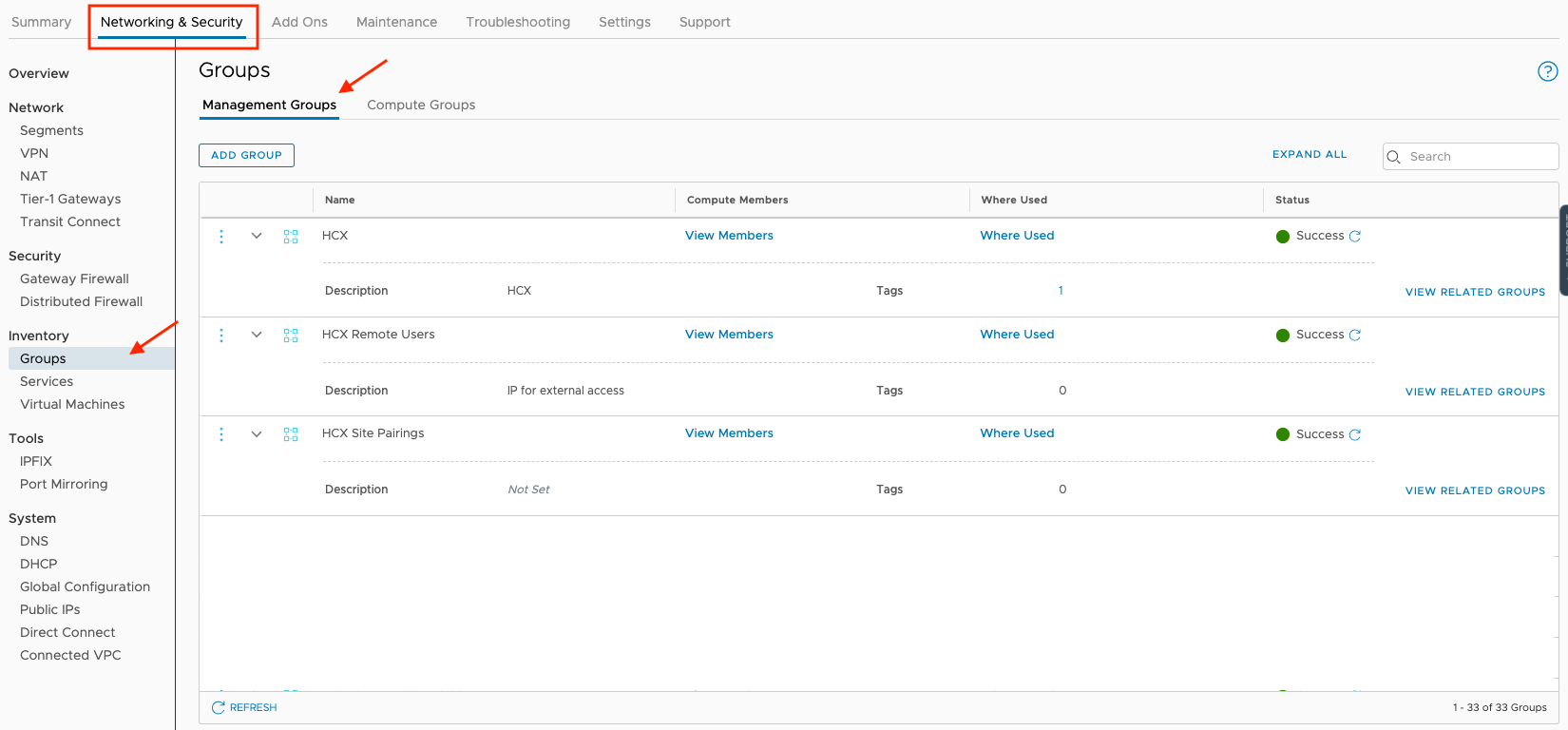
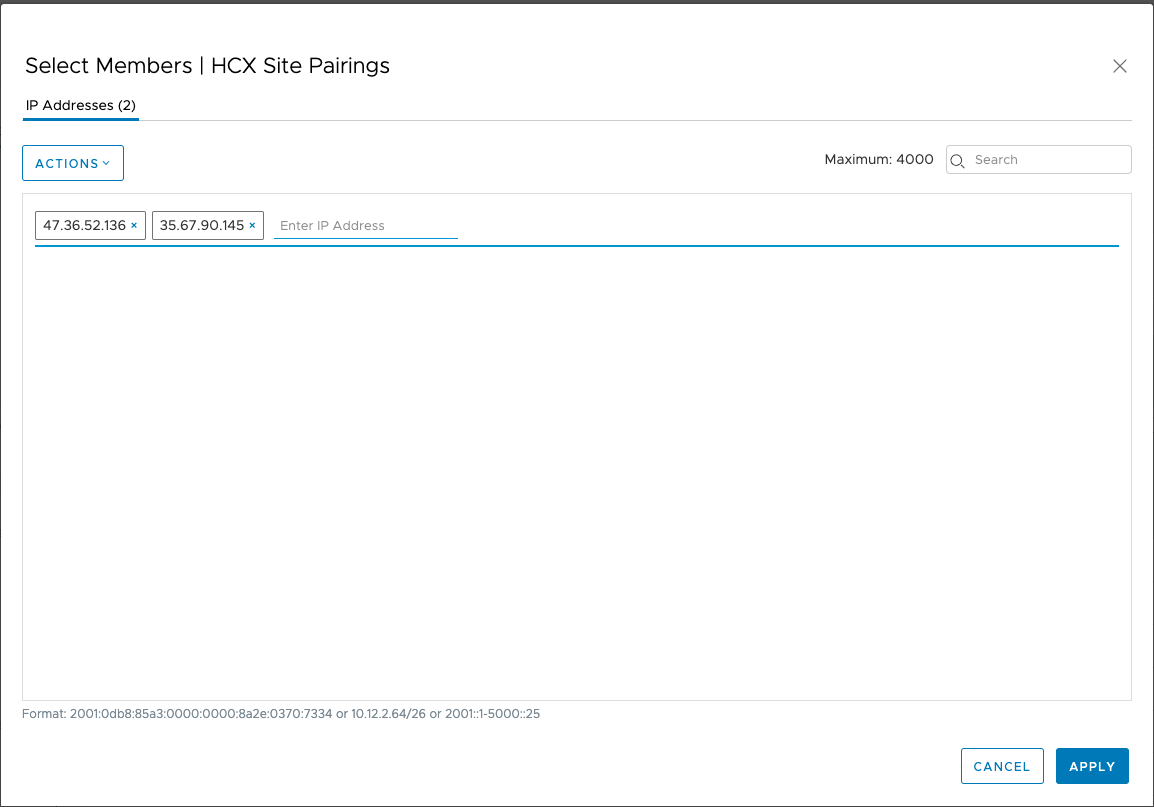
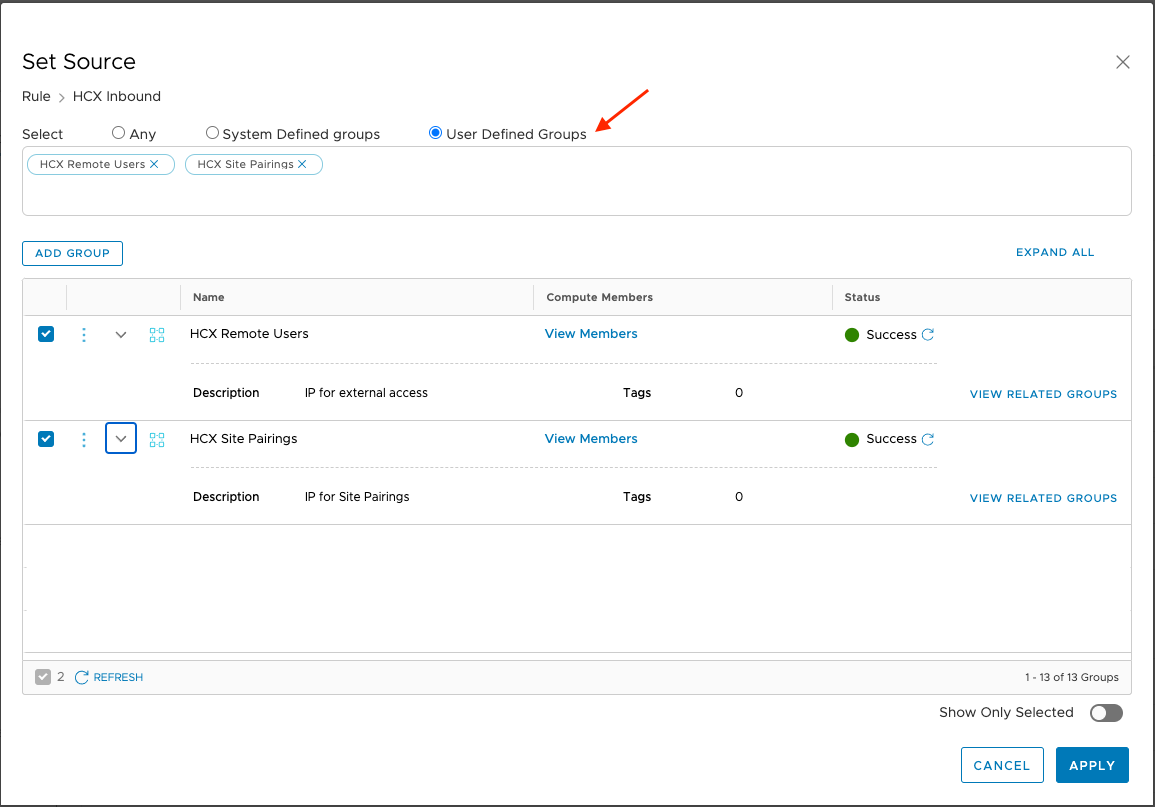
- Got to "Inventory" => "Groups" => "Management Groups" to add User Defined Groups to include the list of source IP addresses that will be allowed to connect to the HCX Cloud Manager through the Management Gateway
- It would be best to use separate User Defined Groups for Remote Access and Site Pairings.
- Consider the fact that the original source IP may be changed through NAT or HTTP Proxy so the external IP address must be configured instead. The Networking Team or Service Provider will be able to provide that information.
- The source IP of Site Pairings established over DX or VPN must also be included in this FW rule despite those being internal.
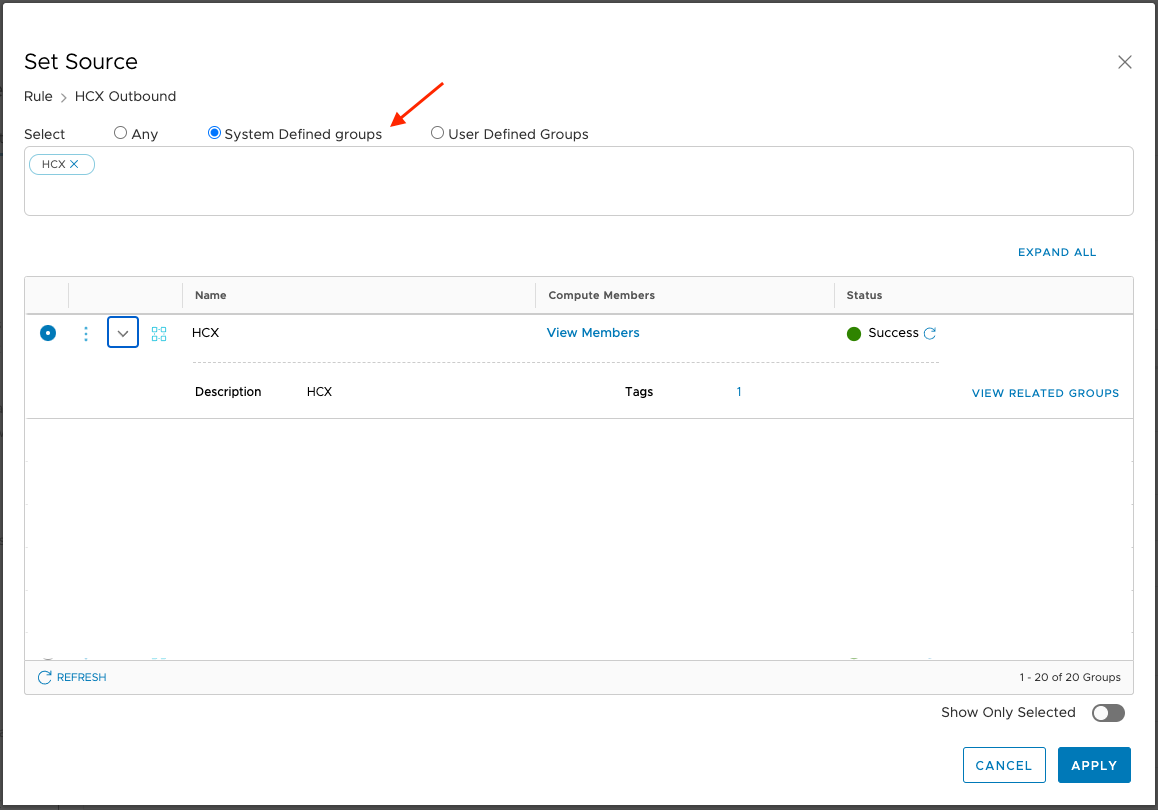
- A group is already defined for the HCX Cloud Manager itself.
- To allow Cloud to Cloud Site Pairings, the CGW SNAT from the remote SDDC must be included in the list.
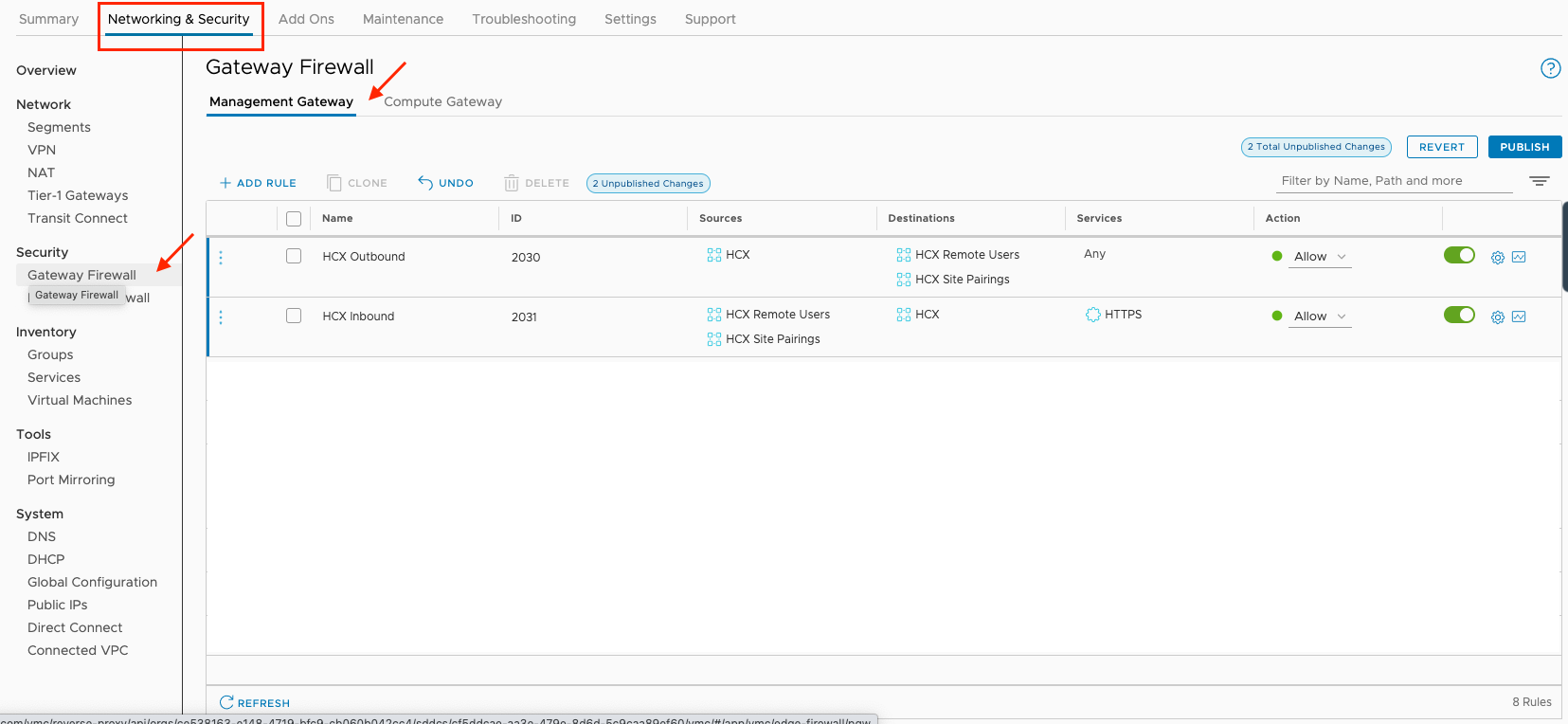
- Navigate to the "Security" => "Gateway Firewall" => "Management Gateway" tab to create the Firewall rules
- Configure an Inbound and the corresponding Outbound rule.
- The recommendation is to limit communication to "HTTPS" only
- Select the "HCX" System Defined Group and the User Defined Groups as required per the direction of each rule.
IMPORTANT: If these rules are created after the Site Pairings were established, verify those remain UP after the rules are applied, to ensure there is no impact due to misconfigurations.
Feedback
Yes
No
