"Error loading data" in DRS configuration wizard in vCenter 7.0 Update 3c or later when logged in with an AD account
Article ID: 326205
Updated On:
Products
VMware vCenter Server
Issue/Introduction
Symptoms:
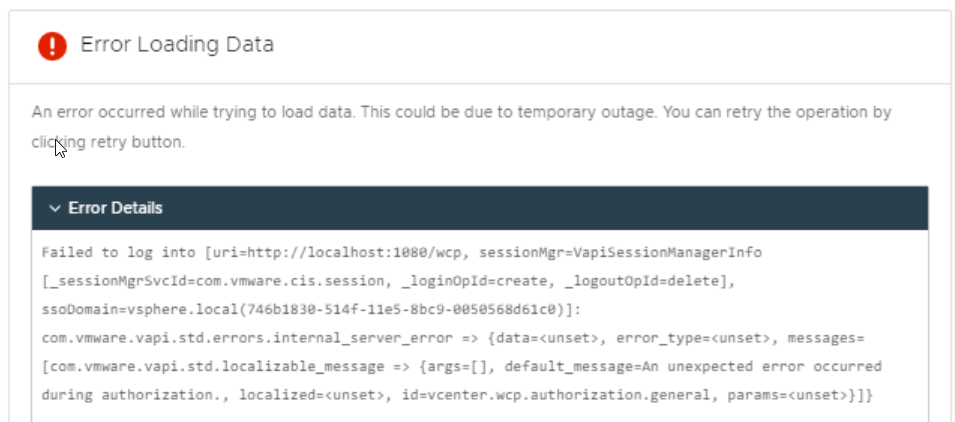
When trying to edit the DRS configuration for a cluster using vSphere Client in vCenter Server 7.0 Update 3c or later while logged in with an Active Directory Account, an error message similar to the image below is shown:
At the same time, /var/log/vmware/vpxd-svcs/vpxd-svcs.log contains errors like this:
When trying to edit the DRS configuration for a cluster using vSphere Client in vCenter Server 7.0 Update 3c or later while logged in with an Active Directory Account, an error message similar to the image below is shown:
At the same time, /var/log/vmware/vpxd-svcs/vpxd-svcs.log contains errors like this:
vpxd-svcs.log
2022-03-25T13:26:43.726Z [tomcat-exec-46 ERROR com.vmware.cis.core.authz.accesscontrol.impl.AuthzServiceBaseImpl opId=6b7441fa-9872-4757-a997-5fdfec4e0beb] Store Exception
java.lang.IllegalArgumentException: Invalid principal name my_user_group@[email protected]
at com.google.common.base.Preconditions.checkArgument(Preconditions.java:217)
at com.vmware.cis.core.util.NormalizedPrincipalHelper.getNormalizedPrincipal(NormalizedPrincipalHelper.java:30)
at com.vmware.cis.authorization.impl.PrincipalImpl.<init>(PrincipalImpl.java:19)
at com.vmware.cis.authorization.impl.AclPrivilegeValidator.getPrincipal(AclPrivilegeValidator.java:232)
at com.vmware.cis.authorization.impl.AclPrivilegeValidator.isAllowed(AclPrivilegeValidator.java:146)
at com.vmware.cis.authorization.impl.AclPrivilegeValidator.isAllowed(AclPrivilegeValidator.java:135)Environment
VMware vCenter Server 7.0.3
Cause
The issue is being caused by the Active Directory account of the logged in user being a member of an Active Directory Group, whose name contains a special character vCenter cannot currently handle, like "@"
Resolution
This issue has been resolved in vCenter Server 7.0 Update 3f. Please refer to Build numbers and versions of VMware vCenter Server (2143838) for the specific build number for this release.
Workaround:
As a workaround, please do not use Active Directory groups with a "@" character in their name. If this is not an option, you can also remove affected users from such groups.
Feedback
Yes
No
