Dell EMC Avamar 18.2 for VMware Cloud on AWS
Article ID: 324699
Updated On:
Products
VMware Cloud on AWS
Issue/Introduction
This article provides information about Dell EMC Avamar 18.2 support for VMware Cloud on AWS. With Dell EMC Avamar 18.2, you can administrate backup, replication and restore operations in VMware Cloud on AWS environments.
Disclaimer: The partner solution referenced in this article is a solution that is developed and supported by a partner. Use of this product is also governed by the end user license agreement of the partner. You must obtain from the partner the application, support, and licensing for using this product. For more information, see Dell EMC Avamar.
Disclaimer: The partner solution referenced in this article is a solution that is developed and supported by a partner. Use of this product is also governed by the end user license agreement of the partner. You must obtain from the partner the application, support, and licensing for using this product. For more information, see Dell EMC Avamar.
Resolution
Summary of target use cases, solution architecture, solution components, and support information:
Dell EMC Avamar 18.2 and later release provide you with the ability to perform virtual machine protection and recovery by using the Dell EMC Avamar VMware Protection solution. Refer to the Dell EMC Avamar 18.2 for VMware user guide for all the supported usecases for image based virtual machine protection.
Use cases that are not supported on VMware Cloud on AWS
Some of the VMware features and permissions are not granted within the VMware Cloud on AWS (VMC) environment. Thus, some dependent Dell EMC Avamar features will be limited or not operating. Depending on VMware update releases for VMware Cloud on AWS, the situation may change and the features listed below may become available to be qualified and supported by Dell EMC.
Dell EMC Avamar VMware Protection in VMware Cloud on AWS does not currently support the following operations:
This solution allows image based (via VADP) data protection for the workloads running in VMware Cloud on AWS.
Prerequisites:
Dell EMC Avamar VMware Protection solution in VMware Cloud on AWS requires the following software:
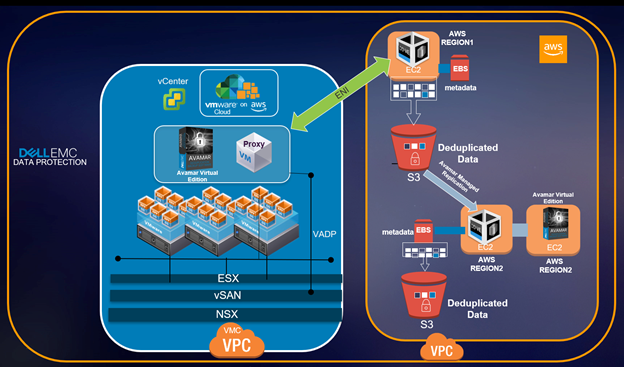
Topology 1:
DataDomain appliances running in AWS VPC for both backup copy as well as replication copy, as EC2 instances. Both DataDomain appliances running in different AWS regions as a best practice.
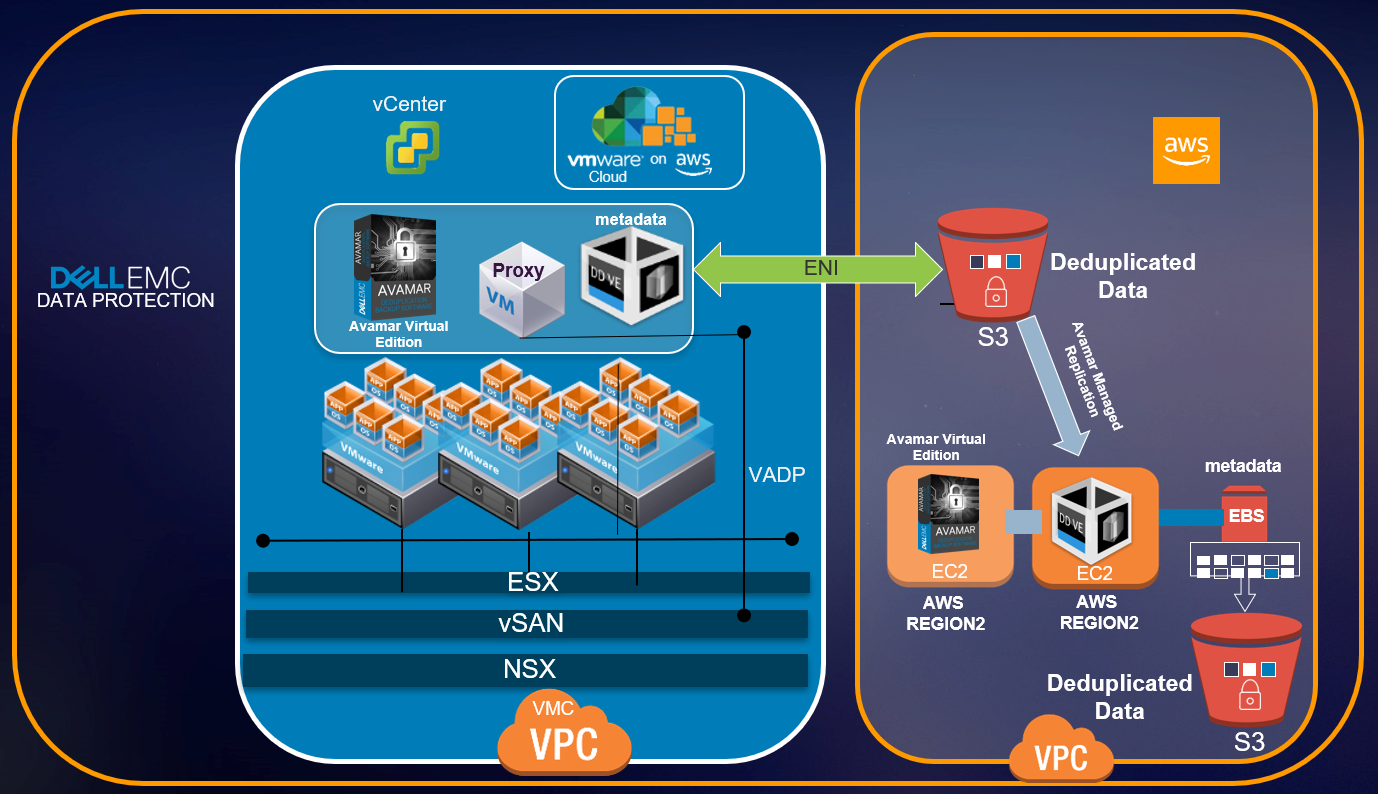
Topology 2:
DataDomain appliance running in VMC VPC (needs minimum version of DDVE 4.0) for the backup copy, with the backup data being stored in S3 object store of AWS VPC . DataDomain appliance for the replication copy running in the AWS VPC as a EC2 instance. Both DataDomain appliances running indifferent AWS regions as a best practice.
To perform data protection and disaster recovery tasks in VMware Cloud on AWS, consider the following recommendations and requirements on the backup infrastructure deployment:
VMware Cloud on AWS web portal console
In the “VMware Cloud on AWS” web portal console please ensure the following: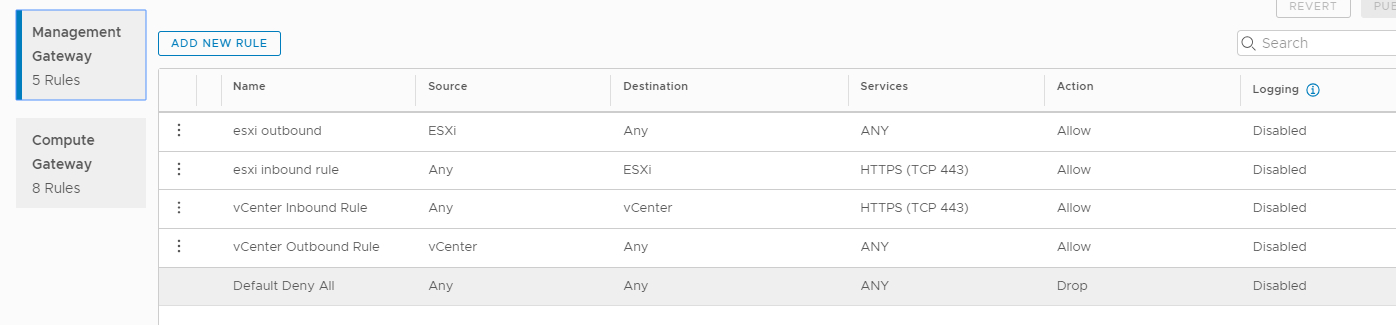
Amazon AWS web portal
In the “Amazon AWS” web portal, note the following requirements:
vCenter Server inventory
In the vCenter server inventory of your SDDC, note the following requirements: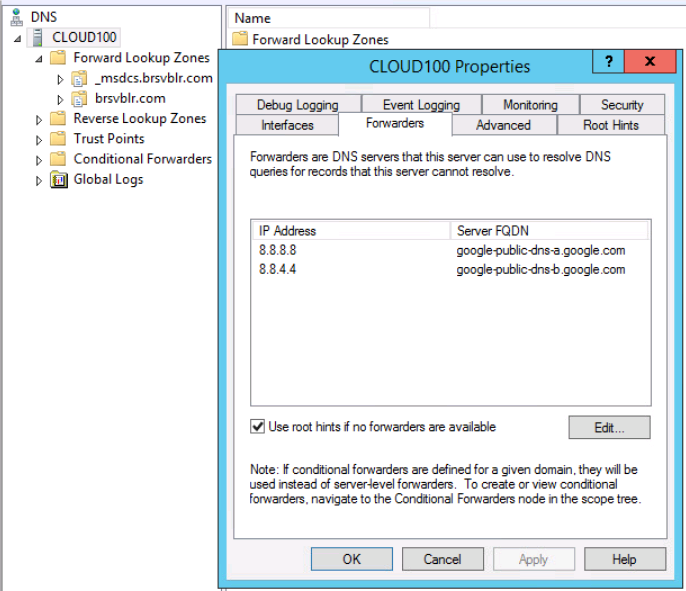
Interoperability with VMware Cloud on AWS product features
VMware Cloud on AWS has certain restrictions when it comes to workloads and resource pools. For proper operation, you can select the specific areas marked as “Workload” or “Compute”. Avoid using the non-accessible areas, for example:
Steps to import the authentication certificates for VMware Cloud on AWS:
For AUI (HTML5 Avamar Administration console) using vCenter authentication to work, ensure you apply the server hotfix hotfix v18_2_0_134_HF_201903 or later.
Note: For a more detailed example on how to apply an AVP-based hotfix, you can refer to the article - https://support.emc.com/kb/501620.
For VMware Protection using Avamar Proxy, please refer to the appendix “Troubleshooting” in Dell EMC Avamar 18.2 for VMware user guide
Documentation available at https://support.emc.com/products/759_Avamar-Server/Documentation/ provides additional and detailed information on setup as well as configuration for all of the solution components.
Target usecases
Use cases that are supported on VMware Cloud on AWSDell EMC Avamar 18.2 and later release provide you with the ability to perform virtual machine protection and recovery by using the Dell EMC Avamar VMware Protection solution. Refer to the Dell EMC Avamar 18.2 for VMware user guide for all the supported usecases for image based virtual machine protection.
Use cases that are not supported on VMware Cloud on AWS
Some of the VMware features and permissions are not granted within the VMware Cloud on AWS (VMC) environment. Thus, some dependent Dell EMC Avamar features will be limited or not operating. Depending on VMware update releases for VMware Cloud on AWS, the situation may change and the features listed below may become available to be qualified and supported by Dell EMC.
Dell EMC Avamar VMware Protection in VMware Cloud on AWS does not currently support the following operations:
- Proxy Deployment Manager for deployment of proxies
- Instant access recovery of an image-level backup.
- Emergency restore (image-level restore directly to an ESXi host, bypassing the vCenter).
- Image-level backups and restores using NBD or NBDSSL transport mode.
- Advanced policy based data protection for MS-SQL using Avamar.
- Application aware image backups for MS-SQL and MS-Exchange
- Image backup and restore when the datacenter is under a folder
- Exclusion of pagefile or user defined files from Windows image backup
- Proxy appliance configured with “dual stack” or “IPv6 only” is not supported
- VMware tag based rule selection criteria for dynamic policy
- Use of the vSphere HTML5 plugin for the vCenter
Solution Architecture
Dell EMC Avamar VMware Protection for VMware Cloud on AWSThis solution allows image based (via VADP) data protection for the workloads running in VMware Cloud on AWS.
Prerequisites:
Dell EMC Avamar VMware Protection solution in VMware Cloud on AWS requires the following software:
- Dell EMC Avamar Virtual Edition Server 18.2 with hotfix v18_2_0_134_HF_201903 or later
HF is available at following location:
ftp://avamar_ftp:[email protected]/software/hotfixes/307714/v18_2_0_134_mc_cumulative_201903.avp
Use WinSCP, or similar means to upload the avp package to avamar server into the following location:
/data01/avamar/repo/packages
Login workflow page and follow the instructions to install the hot fix avp automatically
NOTE: For a more detailed example on how to apply an AVP-based hotfix, you can refer to the following KB: https://support.emc.com/kb/501620
Use WinSCP, or similar means to upload the avp package to avamar server into the following location:
/data01/avamar/repo/packages
Login workflow page and follow the instructions to install the hot fix avp automatically
NOTE: For a more detailed example on how to apply an AVP-based hotfix, you can refer to the following KB: https://support.emc.com/kb/501620
- Data Domain Virtual Edition (DDVE) version 3.1 or later
- Avamar proxy appliance version 18.2 with hotfix 18_2_100-134_HF_310458 or later
HF is available at following location:
ftp://avamar_ftp:[email protected]/software/hotfixes/310458/SLES12SP1_64/AvamarVMwareCombined-linux-sles12sp1-x86_64-18.2.100-134.rpm
To install this patch, copy the RPM provided in this hotfix to the /tmp directory on your running Proxy Appliance.
Log into the VMware Appliance as root and cd /tmp
Proceed to install the RPM running the following command:
rpm -Uvh --force AvamarVMwareCombined-linux-sles12sp1-x86_64-18.2.100-134.rpm
Delete the RPM after installation from the /tmp directory and reboot the appliance.
Repeat steps 1-4 for each proxy that is deployed in the environment.
Your Avamar configuration is now ready for use.
ftp://avamar_ftp:[email protected]/software/hotfixes/310458/SLES12SP1_64/AvamarVMwareCombined-linux-sles12sp1-x86_64-18.2.100-134.rpm
To install this patch, copy the RPM provided in this hotfix to the /tmp directory on your running Proxy Appliance.
Log into the VMware Appliance as root and cd /tmp
Proceed to install the RPM running the following command:
rpm -Uvh --force AvamarVMwareCombined-linux-sles12sp1-x86_64-18.2.100-134.rpm
Delete the RPM after installation from the /tmp directory and reboot the appliance.
Repeat steps 1-4 for each proxy that is deployed in the environment.
Your Avamar configuration is now ready for use.
Topology 1:
DataDomain appliances running in AWS VPC for both backup copy as well as replication copy, as EC2 instances. Both DataDomain appliances running in different AWS regions as a best practice.
Topology 2:
DataDomain appliance running in VMC VPC (needs minimum version of DDVE 4.0) for the backup copy, with the backup data being stored in S3 object store of AWS VPC . DataDomain appliance for the replication copy running in the AWS VPC as a EC2 instance. Both DataDomain appliances running indifferent AWS regions as a best practice.
To perform data protection and disaster recovery tasks in VMware Cloud on AWS, consider the following recommendations and requirements on the backup infrastructure deployment:
- Avamar Server: it is recommended to deploy Dell EMC Avamar server in VMware Cloud on AWS environment as a virtual appliance (AVE).
- Avamar Image Proxy: it is recommended to deploy the proxy appliance in VMware Cloud on AWS environment. Deploy at least one image proxy per each SDDC cluster in the VMware Cloud on AWS.
- Data Domain Virtual Edition: it is recommended to have your backups stored outside of the VMware Cloud on AWS environment, for example, on the Amazon AWS VPC. This type of deployment allows for efficient data transfer over the fast ENI connection used by VMware to communicate with Amazon AWS.
It is also recommended to replicate your backups to another Data Domain running either in the same AWS geographical location or in a different AWS geographical location. This type of deployment allows backup copies to be stored for longer retention, leveraging the AWS network for transferring data at lower latency and cost when compared to the public Internet.
The Dell EMC Avamar 18.2 for VMware user guide provides details on how to set up and configure the Avamar solution for VMware Cloud on AWS.
VMware Cloud on AWS Network configuration
Domain Name System (DNS) resolution is critical for Dell EMC Avamar deployment and configuration. All infrastructure components should be resolvable through a fully qualified domain name (FQDN). This is especially important for the Dell EMC Avamar Server, Dell EMC Avamar image proxy and Data Domain appliance. Resolvable means that components are accessible through both forward (A) and reverse (PTR) look-ups. Review the following prerequisites prior to configuring Dell EMC Avamar in a VMware Cloud on AWS. Also, ensure that you plan your firewall according to these prerequisites:VMware Cloud on AWS web portal console
In the “VMware Cloud on AWS” web portal console please ensure the following:
- By default, there is no external access to the vCenter Server system in your SDDC (Software Defined Data Center). You can open access to your vCenter Server system by configuring a firewall rule. Set the firewall rule in the compute gateway of VMware Cloud on AWS to enable communication to the vCenter public IP address from the desired logical network of your SDDC. The Dell EMC Avamar server will not allow you to add the vCenter Server if this firewall rule is not configured in the SDDC.
- The default compute gateway firewall rules prevent all virtual machine traffic from reaching the internet. To allow your Dell EMC Avamar Server virtual machine to connect to the internet, you need to create a compute gateway firewall rule to allow outbound traffic on the logical network that your Dell EMC Avamar Server virtual machine is connected to.
- Configure DNS to allow machines in your SDDC to resolve fully-qualified domain names (FQDNs) to IP addresses belonging to the internet. The Dell EMC Avamar Server will not allow you to add the vCenter Server using the server's public FQDN or IP address if the DNS server is not configured in your SDDC.
- It is recommended that you deploy the Data Domain system as a virtual appliance in the Amazon VPC (Virtual Private Cloud) of your choice. During the SDDC creation, ensure that you connect your SDDC to an AWS account, and select a VPC and subnet within that account.
- The Data Domain system running in your Amazon VPC must be connected to your VMware SDDC by way of the VMware Cloud Elastic Network Interfaces (ENIs), allowing your SDDC and services in the AWS VPC and subnet in your AWS account to communicate without needing to route traffic through the internet gateway.
- Detailed steps on configuring ENI are provided by VMware at https://vmc.vmware.com/console/aws-link
- Ensure that you configure the inbound and outbound firewall rules of your compute gateway for Data Domain connectivity if DDVE is running in your Amazon VPC.
- If using NSX-T then you need to configure the DNS to resolve to internal IP address of the vCenter (Go to your SDDC Management – Settings – vCenter FQDN and select the Private vCenter IP address) so that you can directly access the management network over the built-in firewall. TCP Port 443 of the vCenter and ESXi needs to be opened(both inbound and outbound) in both the management gateway as well as compute gateway.
Sample of firewall rules configured for FLR(file level restore):
- If using NSX-T for file-level restore operations requires you to update the axionfs.cmd file on the proxy appliances with the IPv4 address of the Avamar server. After you register and activate the Avamar proxy appliances in the Avamar server, log into each of the Avamar proxy appliances as root, and then open the /usr/local/avamar/var/axionfs.cmd file in a UNIX text editor.
Within the file, locate the --server entry key and update the corresponding value to the IPv4 address of the Avamar server. For example, --server=192.168.2.150
Amazon AWS web portal
In the “Amazon AWS” web portal, note the following requirements:
- Configure the inbound and outbound firewall rules of your Amazon VPC security group to provide connectivity between the VMware SDDC compute gateway and Data Domain connectivity if Data Domain is running in your Amazon VPC.
- If replicating from one Data Domain system to another, ensure that you configure the inbound rule for the security group in AWS to allow all traffic from the respective private IPs of Data Domain Virtual Editions running in your Amazon VPC.
- If you have more than one Data Domain running in AWS to perform replication, then ensure that both Data Domain systems can ping each other using the FQDNs.
vCenter Server inventory
In the vCenter server inventory of your SDDC, note the following requirements:
- An internal DNS name lookup server must be running inside the vCenter inventory. This will be referenced by all the workloads running in the VMware SDDC.
- The internal DNS server must have Forwarders enabled to access the internet. This is required in order to resolve the vCenter Server's public FQDN
Interoperability with VMware Cloud on AWS product features
VMware Cloud on AWS has certain restrictions when it comes to workloads and resource pools. For proper operation, you can select the specific areas marked as “Workload” or “Compute”. Avoid using the non-accessible areas, for example:
- vsanDatastore datastore
- Management VMs folder in VMs and Templates view
- Mgmt-ResourcePool resource pool in Hosts and Clusters view
Support Information
Configuration best practices- Please ensure the required hotfixes are applied on top of 18.2 version of Avamar server and proxy. Refer to the Prerequisites section of this KB for details on the hotfixes to be applied
- When deploying or configuring the Dell EMC Avamar server or Image proxy, please ensure that correct DNS server IP pointing to the internal DNS server running in the vCenter inventory is specified.
- Ensure that both forward and reverse lookup entries in the internal DNS server are in place for all the required components such as Dell EMC Avamar server, Dell EMC Avamar Image proxy, DDVE appliance etc.
- If using NSX-T, configure the DNS to resolve to the internal IP address of the vCenter server. Navigate to SDDC Management > Settings > vCenter FQDN and select the Private vCenter IP address so that you can directly access the management network over the built-in firewall.
- If using NSX-T, ensure that you open TCP port 443 of the vCenter and ESXi server in both the management gateway and the compute gateway.
- Using NSX-T, for file-level restore operations requires you to update the axionfs.cmd file on the proxy appliances with the IPv4 address of the Avamar server. After you register and activate the Avamar proxy appliances in the Avamar server, log into each of the Avamar proxy appliances as root, and then open the /usr/local/avamar/var/axionfs.cmd file in a UNIX text editor. Within the file, locate the --server entry key and update the corresponding value to the IPv4 address of the Avamar server. For example, --server=192.168.2.150
- If using NSX-T, add the vCenter server to the Dell EMC Avamar server using either the private IP address or the FQDN, it is recommended to use FQDN.
- When accessing the AUI (HTML5 Avamar Administration console) using vCenter authentication, note the following requirement
Specify the following parameter in the aui.properties file kept in the below path on the Avamar server
/usr/local/avamar/var/aui/server_data/prefs/
vmc.vcenters=vcenter-name
Notes:
- vcenter name has to match as it appears in Avamar Administrator.
- This setting is mandatory for any vCenters running in VMware cloud on AWS, if not set then login to the AUI will fail when using the vCenter Auth.
/usr/local/avamar/var/aui/server_data/prefs/
vmc.vcenters=vcenter-name
Notes:
- vcenter name has to match as it appears in Avamar Administrator.
- This setting is mandatory for any vCenters running in VMware cloud on AWS, if not set then login to the AUI will fail when using the vCenter Auth.
- If using NSX-V, add the vCenter server to the Dell EMC Avamar server using either the public FQDN of the vCenter server or the public IP address of the vCenter server. It is recommended to use FQDN.
- While adding the vCenter server to the Dell EMC Avamar server, specify the login credentials for the [email protected] user.
Configuring vCenter-to-Avamar authentication for VMware Cloud on AWS
The most secure method for configuring vCenter-to-Avamar authentication is to add vCenter authentication certificates to the Avamar MCS keystore. You must do this for each vCenter you intend to protect.Steps to import the authentication certificates for VMware Cloud on AWS:
- Download any root certificate from entrust website - https://www.entrustdatacard.com/pages/root-certificates-download.
- Place the root certificate in the Avamar server and follow the instructions as per documented section "Adding vCenter authentication certificates to the MCS keystore" in the Dell EMC Avamar 18.2 for VMware user guide.
- Proceed to add the vCenter to the Avamar server as per the documented steps.
Troubleshooting:
For image backups and restores to work, please ensure you apply the hotfix 18_2_100-134_HF_310458 or laterHF is available at following location:
ftp://avamar_ftp:[email protected]/software/hotfixes/310458/SLES12SP1_64/AvamarVMwareCombined-linux-sles12sp1-x86_64-18.2.100-134.rpm
To install this patch:
ftp://avamar_ftp:[email protected]/software/hotfixes/310458/SLES12SP1_64/AvamarVMwareCombined-linux-sles12sp1-x86_64-18.2.100-134.rpm
To install this patch:
- Copy the RPM provided in this hotfix to the /tmp directory on your running Proxy Appliance.
- Log into the VMware Appliance as root and cd /tmp
- Proceed to install the RPM running the following command:
rpm -Uvh --force AvamarVMwareCombined-linux-sles12sp1-x86_64-18.2.100-134.rpm
- Delete the RPM after installation from the /tmp directory and reboot the appliance.
- Repeat steps 1-4 for each proxy that is deployed in the environment.
Your Avamar configuration is now ready for use.
For AUI (HTML5 Avamar Administration console) using vCenter authentication to work, ensure you apply the server hotfix hotfix v18_2_0_134_HF_201903 or later.
- HF is available at following location:
- Use WinSCP, or similar means to upload the avp package to avamar server into the following location:
/data01/avamar/repo/packages
Login workflow page and follow the instructions to install the hot fix avp automatically.
Login workflow page and follow the instructions to install the hot fix avp automatically.
Note: For a more detailed example on how to apply an AVP-based hotfix, you can refer to the article - https://support.emc.com/kb/501620.
For VMware Protection using Avamar Proxy, please refer to the appendix “Troubleshooting” in Dell EMC Avamar 18.2 for VMware user guide
Log collection
For VMware Protection using Avamar Proxy, all relevant logs are placed in the below locations:- Avamar Server: /space/avamar/var/mc/server_log/
- Avamar Proxy: /usr/local/avamarclient/var/
Documentation available at https://support.emc.com/products/759_Avamar-Server/Documentation/ provides additional and detailed information on setup as well as configuration for all of the solution components.
Feedback
Yes
No
