NSX Network Detection and Response - Sensor: Pcap snipping feature
Article ID: 323941
Updated On:
Products
VMware
Issue/Introduction
Currently this article is applicable ONLY to sensor versions < 1320 hosted and 1371 for on-premise, the override will be available again in version 1390 for both hosted and on-premise.
Some signature hits and corresponding events have traffic captures (pcaps) and some does not.
The IDS service (Suricata) keeps in memory a buffer of recent packets for each flow it analyzes, so that, when an alert is generated, the corresponding buffer is dumped to a pcap file. However, the pcap snipping mechanism is memory constrained: if the IDS service cannot keep all the packets in the buffer, it will throw away the least recent ones.
Based on this, the appliance might not be able to generate a pcap for a given alert for the following reasons:
When it comes to buffer size, the buffer size needs are directly proportional to the number of concurrent flows expected on a given appliance, as well as the configured MTU (sensors with larger MTUs will use more memory to store packets).
Some signature hits and corresponding events have traffic captures (pcaps) and some does not.
The IDS service (Suricata) keeps in memory a buffer of recent packets for each flow it analyzes, so that, when an alert is generated, the corresponding buffer is dumped to a pcap file. However, the pcap snipping mechanism is memory constrained: if the IDS service cannot keep all the packets in the buffer, it will throw away the least recent ones.
Based on this, the appliance might not be able to generate a pcap for a given alert for the following reasons:
- The appliance allocate memory for the pcap snipping feature based on the resources available to the appliance. With a minimum of 1GB of buffer, recent appliances allow the buffer to take 40% of the memory available to the sniffing component. Older appliances (<1360) instead statically allocated only 2GB of RAM.
- It is known from threat intelligence data that the alerts are normally triggering at the very beginning of a flow. When encountering the so-called "elephant flows", likely to be associated to backups or large file transfers, we optimize CPU utilization by no longer tracking the pcap data. This happens by default after the first 8MB of data transferred by a flow. If an alert triggers that deep into a flow, it is very likely that the alert is a false positive.
When it comes to buffer size, the buffer size needs are directly proportional to the number of concurrent flows expected on a given appliance, as well as the configured MTU (sensors with larger MTUs will use more memory to store packets).
Resolution
The pcap snipping feature is a best-effort approach due to the limited amount of buffer available on the IDS service.
However, there is an override parameter that can be applied to specify how deep in the flow we want to allow a pcap snip to be generated and will most likely eliminate the problem of missing pcap files keeping always in mind that if the sensor runs out of buffer, will not be able to generate a pcap.
Note: Use this override (at your own risk) only in environments where sensors do not have to process a high amount of traffic.
Sensors having this override in place will experience significant packet processing performance degradation and it will have no benefits on event detection/correlation, it is merely to force the sensor to always save the traffic captured during the event timeline and make it available for download in the Event Profile section.
Procedure:
1. ssh into the sensor.
2. Add the override to the /etc/appliance-config/override.yaml file or create the file if it does not exist:
echo 'suricata::suricata_lastline::pcap_snipping_flow_max_depth: 67108864' >> /etc/appliance-config/override.yaml
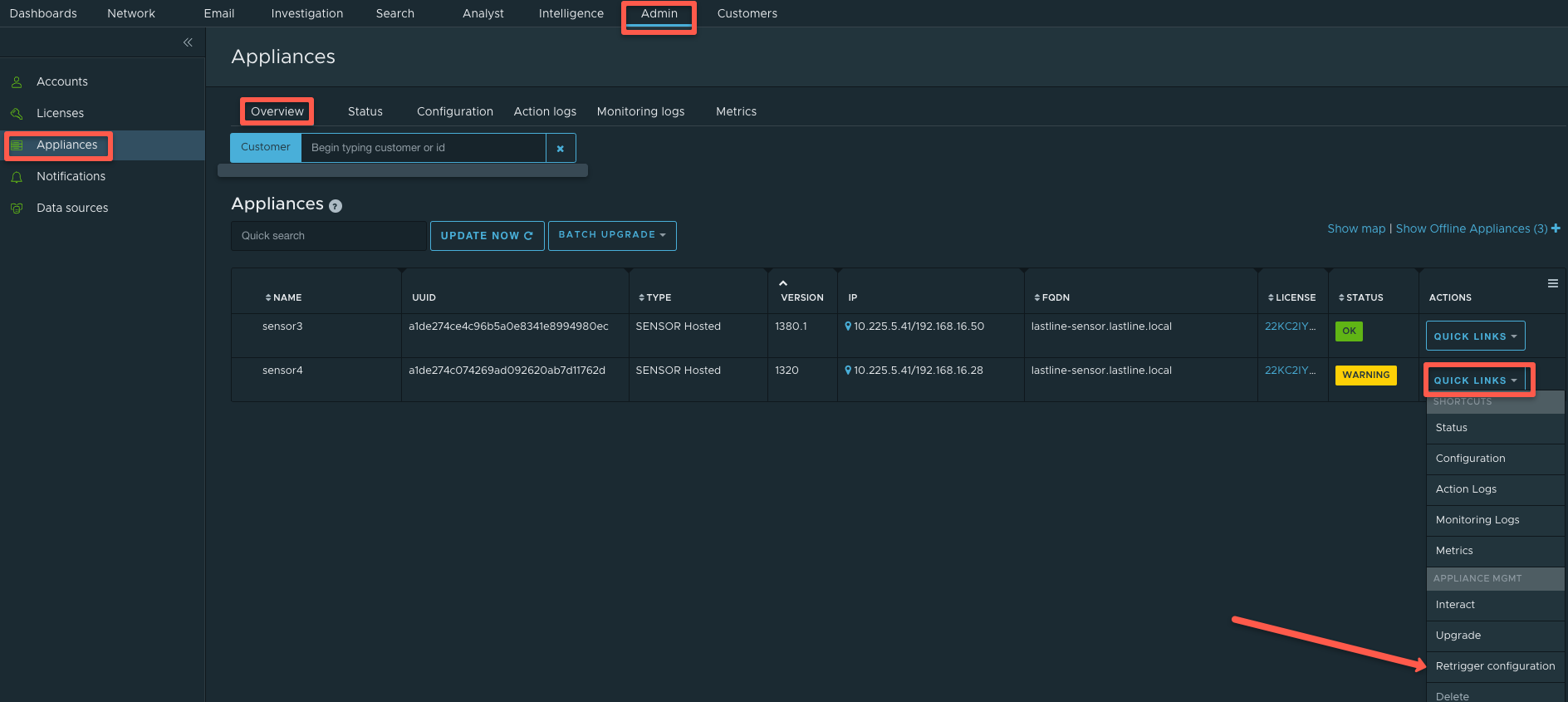
3. Retrigger the configuration from the UI. To do so go to: Admin > Appliances > Overview > Select the sensor > Quick Links > Retrigger Configuration and wait for it to finish.
However, there is an override parameter that can be applied to specify how deep in the flow we want to allow a pcap snip to be generated and will most likely eliminate the problem of missing pcap files keeping always in mind that if the sensor runs out of buffer, will not be able to generate a pcap.
Note: Use this override (at your own risk) only in environments where sensors do not have to process a high amount of traffic.
Sensors having this override in place will experience significant packet processing performance degradation and it will have no benefits on event detection/correlation, it is merely to force the sensor to always save the traffic captured during the event timeline and make it available for download in the Event Profile section.
Procedure:
1. ssh into the sensor.
2. Add the override to the /etc/appliance-config/override.yaml file or create the file if it does not exist:
echo 'suricata::suricata_lastline::pcap_snipping_flow_max_depth: 67108864' >> /etc/appliance-config/override.yaml
3. Retrigger the configuration from the UI. To do so go to: Admin > Appliances > Overview > Select the sensor > Quick Links > Retrigger Configuration and wait for it to finish.
Additional Information
Note: This article is applicable to the standalone NSX Network Detection and Response product (formerly Lastline) and is not intended to be applied to the NSX NDR feature of NSX-T.
Feedback
Yes
No
