[VMC on AWS] Unable to login to NSX manager using AD account credentials
Article ID: 313635
Updated On:
Products
VMware Cloud on AWS
Issue/Introduction
This article provides information about a known issue with adding on-premises Active Directory over LDAP and workaround for the issue.
Symptoms:
Unable to login to NSX manager using AD account credentials gives an error "Can't connect to LDAP server" and also receive username/password combination incorrect if try to use different username formats.
Similar Log entries would be found when customer tries to Log in:
<99>1 2022-10-03T05:27:58.598Z NSX-Manager-1 java - - - pam_listfile(nsx-local-pam:auth): Refused user internal\user for service nsx-local-pam2022-10-03 <99>1 2022-10-03T05:27:58.235Z NSX-Manager-1 NSX 4010 SYSTEM [nsx@6876 audit="true" comp="nsx-manager" level="INFO" subcomp="http"] UserName="internal\[email protected]", ModuleName="ACCESS_CONTROL", Operation="LOGIN", Operation status="failure"2022-10-03 10:57:52.660 +0530
Cause
It is a known issue in the 1.20 SDDC version
Resolution
It is a known issue in the v1.20.x release and will be fixed in 1.22.x release.
Workaround:
To configure on-premises Active Directory over LDAP port 389 in M20 we need to toggle the "StartTLS" option until the permanent fix is applied.
Please find a reference screenshot below:
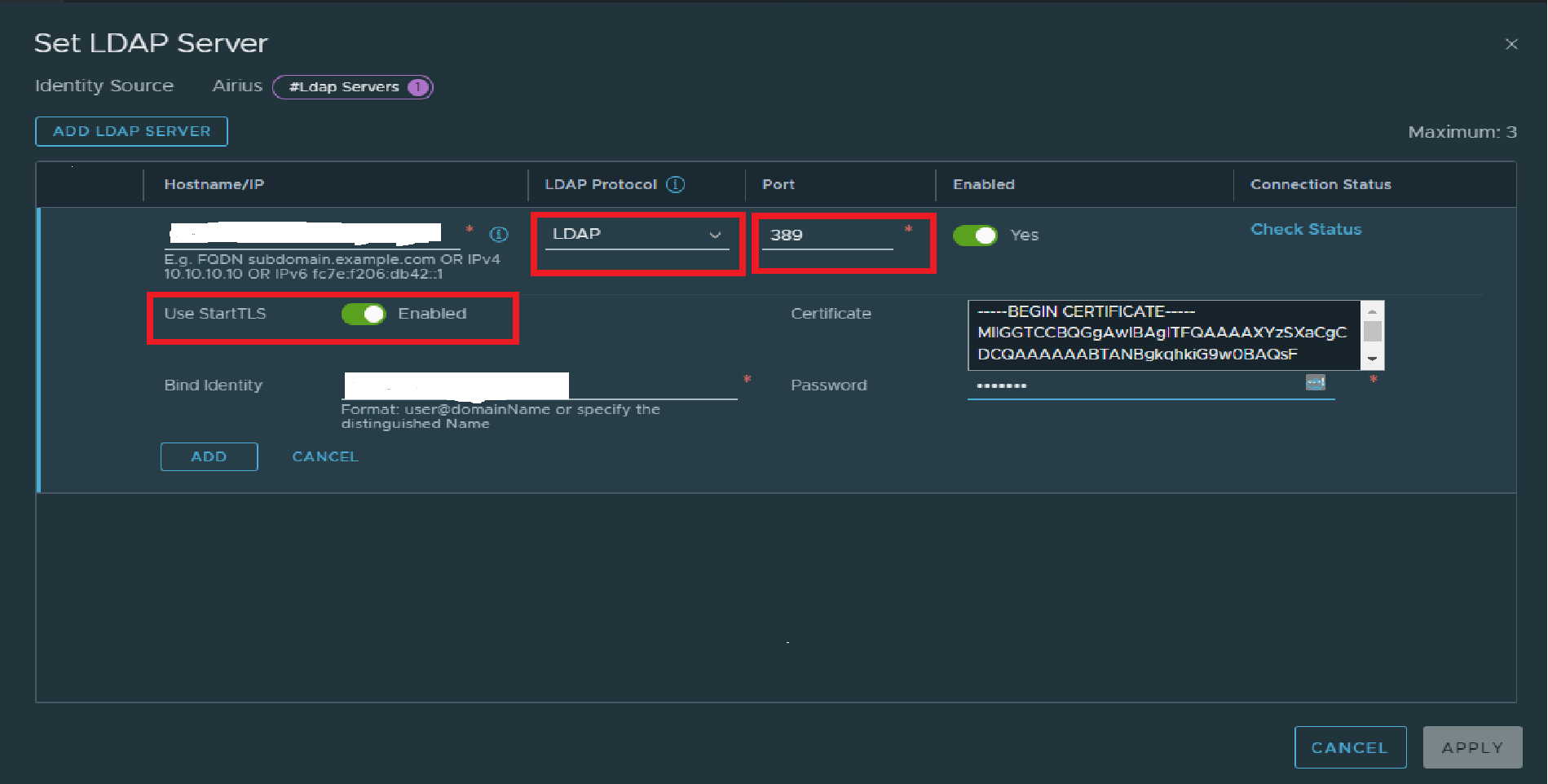
Workaround:
To configure on-premises Active Directory over LDAP port 389 in M20 we need to toggle the "StartTLS" option until the permanent fix is applied.
Please find a reference screenshot below:
Additional Information
LDAP Identity Source: https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/administration/GUID-664DC51F-3D6B-442F-9C29-2A5304ACCCA4.html
Impact/Risks:
Customers are unable to login to NSX managers using AD credentials to manage/perform any actions.
Impact/Risks:
Customers are unable to login to NSX managers using AD credentials to manage/perform any actions.
Feedback
Yes
No
