TAS VMs running AntiVirus impacted by Unix.Malware.Kaiji-10003916-0
Article ID: 297938
Updated On:
Products
VMware Tanzu Application Service for VMs
Issue/Introduction
On Jun 7 07:24:15, ClamAV added a new Detection Signature Unix.Malware.Kaiji-10003916-0 to its list.
https://lists.clamav.net/pipermail/clamav-virusdb/2023-June/008314.html
This was reported as causing many false positives, and was removed at 23:46:10 UTC 2023
https://lists.clamav.net/pipermail/clamav-virusdb/2023-June/008315.html
If you are running Anti-Virus for VMware Tanzu, you're scheduled scan may have picked up on this addition. It has been observed to detect some of the binary files/packages used by the TAS VMs, and can move these to an incorrect directory depending on the Anti-Virus configuration.
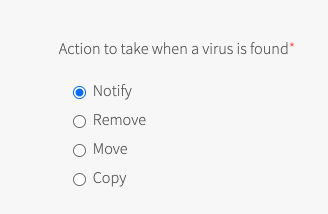
In the Anti-Virus tile, we have the option to determine which action to perform on the detected files. See the following screenshot:
Consider an example from an environment that has the Anti-Virus configuration set to "Move", on a diego cell, it may move /var/vcap/packages/grootfs/bin/grootfs to the /var/vcap/data/antivirus/found directory. If this garden process is restarted on the VM, it will be unable to find the package, and cannot start.
garden.stdout.log
The above is just one example, similar errors may be observed for many processes across any VM deployed.
You can verify any action has been taken on your VMs by:
If you would like to check on all VMs across an entire deployment, then a command similar to the following should help ssh into each instance in the deployment:
If you would like to check all deployments then create the following script, make it executable, and execute where your bosh cli is pointed to your environment:
The output should include all VMs that match the search criteria. Please review the output to isolate which VMs are impacted.
*Please note that you may need to modify the above commands to fit your environment. For example, if you use the -e flag when executing bosh cli commands.
https://lists.clamav.net/pipermail/clamav-virusdb/2023-June/008314.html
This was reported as causing many false positives, and was removed at 23:46:10 UTC 2023
https://lists.clamav.net/pipermail/clamav-virusdb/2023-June/008315.html
If you are running Anti-Virus for VMware Tanzu, you're scheduled scan may have picked up on this addition. It has been observed to detect some of the binary files/packages used by the TAS VMs, and can move these to an incorrect directory depending on the Anti-Virus configuration.
In the Anti-Virus tile, we have the option to determine which action to perform on the detected files. See the following screenshot:
If the selection is Notify - the environment should not be impacted.
If the selection is Remove - the environment may be impacted.
If the selection is Move - the environment may be impacted.
If the selection is Copy - the environment should not be impacted.
Consider an example from an environment that has the Anti-Virus configuration set to "Move", on a diego cell, it may move /var/vcap/packages/grootfs/bin/grootfs to the /var/vcap/data/antivirus/found directory. If this garden process is restarted on the VM, it will be unable to find the package, and cannot start.
garden.stdout.log
"level":"error","source":"guardian","message":"guardian.image-plugin-metrics.image-plugin-result","data":{"action":"metrics","error":"fork/exec /var/vcap/packages/grootfs/bin/grootfs: no such file or directory
The above is just one example, similar errors may be observed for many processes across any VM deployed.
You can verify any action has been taken on your VMs by:
- bosh ssh to a VM
- cd /var/vcap/sys/log/antivirus
- cat * | grep "Unix.Malware.Kaiji-10003916-0"
If you would like to check on all VMs across an entire deployment, then a command similar to the following should help ssh into each instance in the deployment:
bosh -d <deployment-name> ssh -c "sudo grep 'Unix.Malware.Kaiji-10003916-0' /var/vcap/sys/log/antivirus/*"
If you would like to check all deployments then create the following script, make it executable, and execute where your bosh cli is pointed to your environment:
for deployment in `bosh deployments --column=name` do bosh -d $deployment ssh -c "sudo grep 'Unix.Malware.Kaiji-10003916-0' /var/vcap/sys/log/antivirus/*" done
The output should include all VMs that match the search criteria. Please review the output to isolate which VMs are impacted.
*Please note that you may need to modify the above commands to fit your environment. For example, if you use the -e flag when executing bosh cli commands.
Environment
Product Version: 2.1
Resolution
As this signature has been removed from the ClamAV detection list, VMs should no longer be picking up on this.
However, if any VMs have been impacted by this, they will need to be recreated in order to ensure all packages are located in the correct directory again.
If you have an environment impacted from this issue, please open Tanzu Support ticket.
However, if any VMs have been impacted by this, they will need to be recreated in order to ensure all packages are located in the correct directory again.
If you have an environment impacted from this issue, please open Tanzu Support ticket.
Feedback
Yes
No
