Apps Usage errand fails in PAS 2.5 with curl SSL error
Article ID: 297658
Updated On:
Products
VMware Tanzu Application Service for VMs
Issue/Introduction
Symptoms:
The Apps Usage Service errand logs show the following
The Apps Usage Service errand logs show the following
curl error message:
% Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 curl: (60) server certificate verification failed. CAfile: /etc/ssl/certs/ca-certificates.crt CRLfile: none More details here: http://curl.haxx.se/docs/sslcerts.html curl performs SSL certificate verification by default, using a "bundle" of Certificate Authority (CA) public keys (CA certs). If the default bundle file isn't adequate, you can specify an alternate file using the --cacert option. If this HTTPS server uses a certificate signed by a CA represented in the bundle, the certificate verification probably failed due to a problem with the certificate (it might be expired, or the name might not match the domain name in the URL). If you'd like to turn off curl's verification of the certificate, use the -k (or --insecure) option. Error: failed to run job-process: exit status 1 (exit status 1)
Environment
Cause
The Apps Usage Service errand uses native
curl to query an API endpoint instead of cf curl. The native curl command is not influenced by the "skip ssl verification" feature in the PAS deployment.
Resolution
This bug will be fixed in a future version of PAS 2.5 and this article provides two workarounds until this fix is made available.
1. The load balancer or router uses Operations (Ops) Manager generated certificates.
Note: Use this workaround If you Deployed with and Ops Manager generated certificate or have a customer Certificate Authority (CA) installed in Ops Manager.
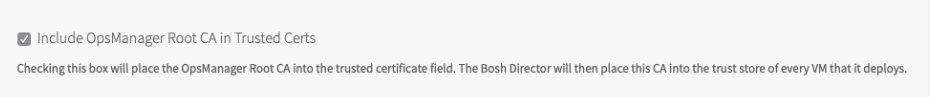
a. Check the box label "Include OpsManager Root CA in Trusted Certs" in the Director Tile > Security Tab. This will force Ops Manager to instruct BOSH to include the Ops Manager configured CA authority into the Operating Systems trusted CAs.
2. The load balancer or router uses a certification signed by a private authority.
a. Include the Certificate Authority in the Trusted Certificates field located in the Director Tile > Security Tab.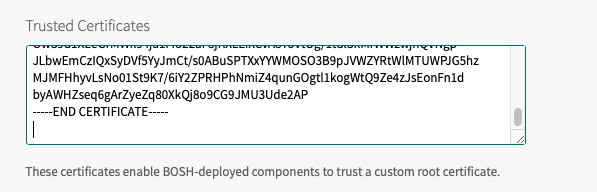
1. The load balancer or router uses Operations (Ops) Manager generated certificates.
Note: Use this workaround If you Deployed with and Ops Manager generated certificate or have a customer Certificate Authority (CA) installed in Ops Manager.
a. Check the box label "Include OpsManager Root CA in Trusted Certs" in the Director Tile > Security Tab. This will force Ops Manager to instruct BOSH to include the Ops Manager configured CA authority into the Operating Systems trusted CAs.
2. The load balancer or router uses a certification signed by a private authority.
a. Include the Certificate Authority in the Trusted Certificates field located in the Director Tile > Security Tab.
Feedback
Yes
No
