How to setup kerberos authentication on gpdb v6 with Windows active directory kerberos.
Article ID: 296953
Updated On:
Products
VMware Tanzu Greenplum
Issue/Introduction
From the official document, it listed steps to implement kerberos authentication with MIT kerberos. But some users may prefer use kerberos service provided by windows active directory. So here are the steps to implement AD
integrated kerberos authentication with GPDB v6.
Environment
Product Version: 6.25
Resolution
Part 1. windows AD and AD kerberos keytab setup
1. This solution is based on windows server 2019, it may also works with windows server 2012 or 2016 or 2022, but not verified.
2. Let's assume the windows server is running normally, means the active directory is working at the domain controller. Normally, the current windows server should be the domain controller, if it's a new install, then you may need to setup a new domain. Here it used "vc.loca" as the current AD domain.
3. create a new user in "Active directory Users and Computers" , choose the correct domain, then "Managed Service Accounts", create a new user. Here "gpdb" user will be used for demostration.
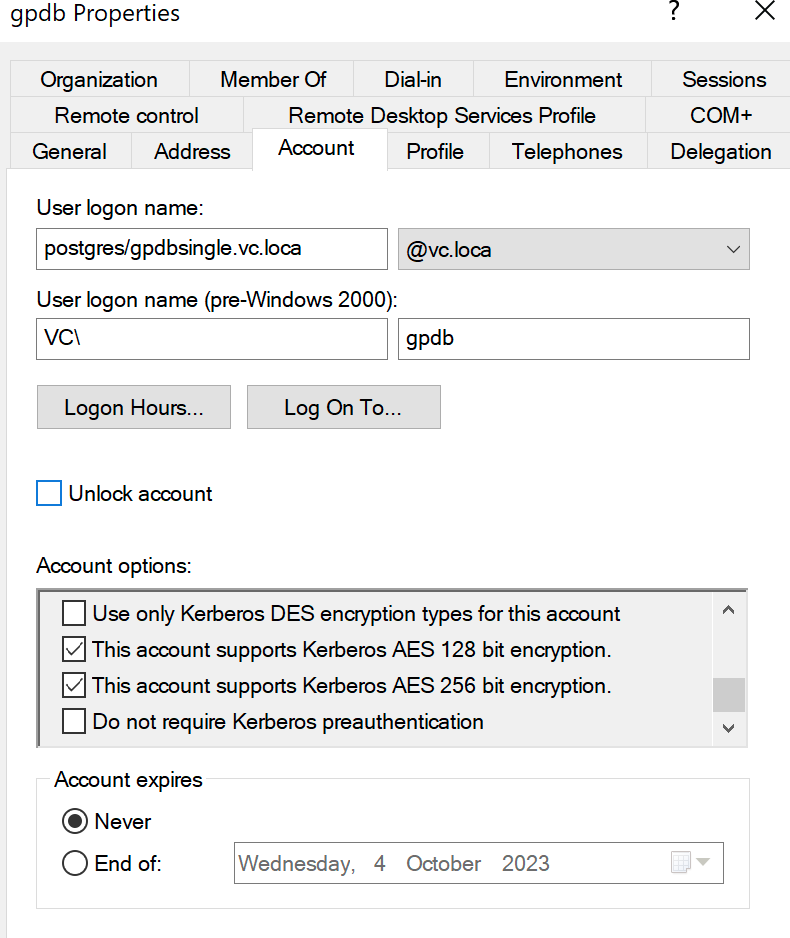
4. After created the user, it's better open it's account properties window, choose "Account", click support Kerberos AES 128/256 bit encryption.
5. Open a powershell, or command window, add service principle for this account :
Part II. DNS server.
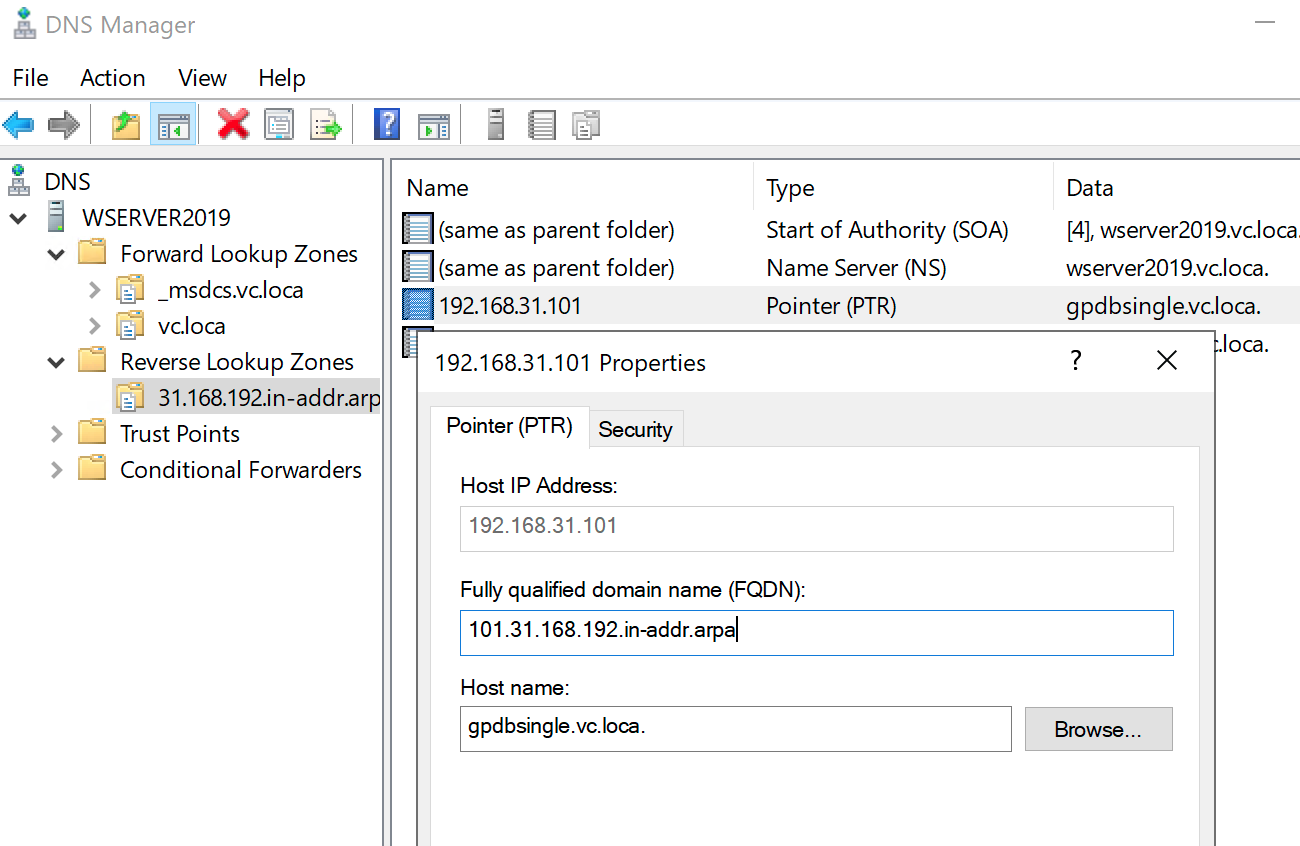
The kerberos authentication process involves hostname lookup, both forward lookup and reverse lookup (from ip -> hostname). We can setup DNS server at the windows server, or on another linux server (with bind service). At the DNS server, it requires entry for both windows server (kerberos server) and gpdb master server.
Part III - GPDB setup.
1. update the postgresql.conf file, add one entry:
7. test login
1. This solution is based on windows server 2019, it may also works with windows server 2012 or 2016 or 2022, but not verified.
2. Let's assume the windows server is running normally, means the active directory is working at the domain controller. Normally, the current windows server should be the domain controller, if it's a new install, then you may need to setup a new domain. Here it used "vc.loca" as the current AD domain.
3. create a new user in "Active directory Users and Computers" , choose the correct domain, then "Managed Service Accounts", create a new user. Here "gpdb" user will be used for demostration.
4. After created the user, it's better open it's account properties window, choose "Account", click support Kerberos AES 128/256 bit encryption.
5. Open a powershell, or command window, add service principle for this account :
setspn -A postgres/gpdbsingle.vc.loca gpdb6. In powershell, or command window, create a keytab with ktpass, this will also update the kerberos database.
ktpass /out gpdb4.keytab /princ gpdb/[email protected] -mapUser gpdb /pass Test#1234 /crypto all /ptype KRB5_NT_PRINCIPAL7. copy this keytab file "gpdb4.keytab" to the master host, change it's owner to database account (like gpadmin). change it's file permission to 400. remember the file location.
Part II. DNS server.
The kerberos authentication process involves hostname lookup, both forward lookup and reverse lookup (from ip -> hostname). We can setup DNS server at the windows server, or on another linux server (with bind service). At the DNS server, it requires entry for both windows server (kerberos server) and gpdb master server.
Part III - GPDB setup.
1. update the postgresql.conf file, add one entry:
krb_server_keyfile = '/data/master/gpseg-1/gpdb4.keytab'2. update pg_hba.conf file, add one entry. This means all remote access will go through kerberos authentication.
host all all 0.0.0.0/0 gss include_realm=0 krb_realm=VC.LOCA3. touch a new file , /etc/krb5.conf, add below content:
# Configuration snippets may be placed in this directory as well
includedir /etc/krb5.conf.d/
[libdefaults]
#default_cc_type = FILE
#default_ccache_name = FILE:/tmp/krb5cc_501
debug = true
# default_etypes = aes256-cts-hmac-sha1-96
dns_lookup_kdc = false
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
# rdns = false
# pkinit_anchors = FILE:/etc/pki/tls/certs/ca-bundle.crt
default_realm = VC.LOCA
#default_ccache_name = KEYRING:persistent:%{uid}
# kdc = wserver2019.vc.loca:88
# admin_server = wserver2019.vc.loca:749
[realms]
VC.LOCA = {
kdc = wserver2019.vc.loca
admin_server = wserver2019.vc.loca
default_realm = VC.LOCA
}
[domain_realm]
.vc.loca = VC.LOCA
vc.loca = VC.LOCA
4. request a ticket from kerberos server: (it should complete directly, no need for password)
kinit -kt gpdb4.keytab "gpdb/admin"5. create the database user " gpdb/admin".
psql, create role "gpdb/admin" login6. reload, gpstop -u
7. test login
psql -h 192.168.31.101 -U "gpdb/admin" gpadmin psql (9.4.26) Type "help" for help. gpadmin=#
Feedback
Yes
No
