Application redirection to OpenID Connect (OIDC) provider fails and UAA screen is blank
Article ID: 293617
Updated On:
Products
Operations Manager
Issue/Introduction
Pre-checks
- SSO plan uses an external Identity provider where the type of the provider is OpenID Connect (tested with Azure AD as the OIDC provider).
This issue could occur when the SSO service instance was unbound and then bounded again with the application.
After the rebind operation succeeds, an application gets registered within SSO and can be found by navigating to the Developer dashboard. When you click on the registered application to view its configurations, you will find out the Identity Providers configured for that application are all unchecked. This is what causes the behavior explained above. When the external Identity Provider is left unchecked, the application request gets redirected to UAA and UAA does not know what authentication method to show because none of the available identity providers is enabled.
For example, Navigate to the SSO Developer dashboard by going to Apps Manager > Org & Space of where the application exists > Click the application name > Go to Services > Click on the SSO service instance bound to the application > Manage. This will open the Developer dashboard - click on the App Name. You will then be able to see that the Select Identity Providers section shows internal as well as external Identity Providers that are configured to use but none of them are selected. Here is a screenshot from a lab environment that shows the same:
Environment
OS: Linux
Resolution
Navigate to the SSO Developer dashboard by going to Apps Manager > Org & Space of where the application exists > Click the application name > Go to Services > Click on the SSO service instance bound to the application > Manage
This will open the Developer dashboard - click on the App Name. You will then be able to see that the Select Identity Providers section shows internal as well as external Identity Providers that are configured to use but none of them are selected.
Enable the one that your use-case requires and update the app by clicking the Update App button at the bottom of the page. Here is how this will look:
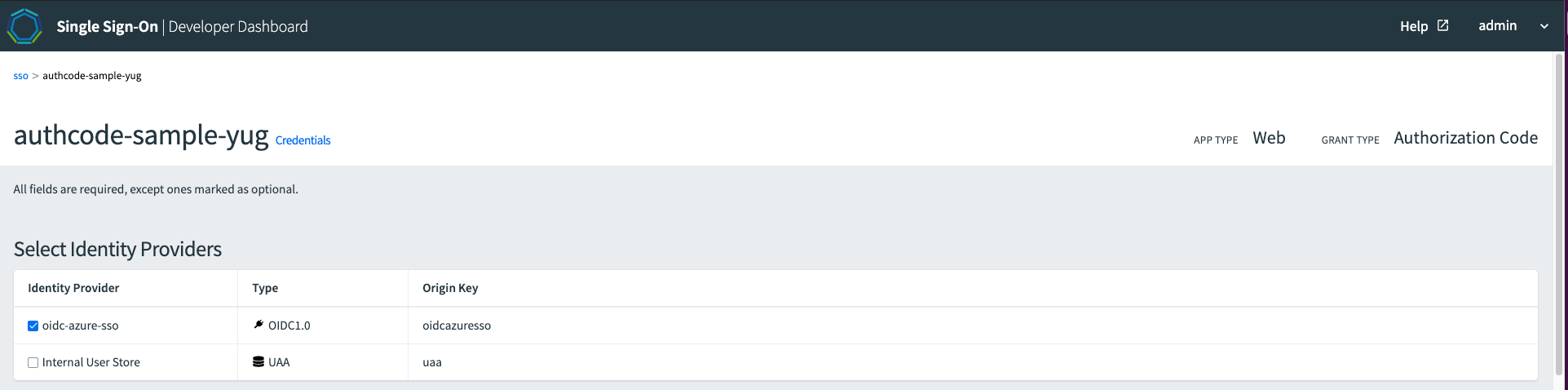
Now you can open the application in the web browser again and you should be redirected to the external identity provider.
This will open the Developer dashboard - click on the App Name. You will then be able to see that the Select Identity Providers section shows internal as well as external Identity Providers that are configured to use but none of them are selected.
Enable the one that your use-case requires and update the app by clicking the Update App button at the bottom of the page. Here is how this will look:
Now you can open the application in the web browser again and you should be redirected to the external identity provider.
Feedback
Yes
No
