EDR: How to Configure Workspace ONE to Deploy Carbon Black Policies for macOS
Article ID: 285256
Updated On:
Products
Carbon Black Hosted EDR (formerly Cb Response Cloud)
Issue/Introduction
How to add the Workstation ONE UEM policies necessary to successfully deploy Carbon Black macOS sensor.
Environment
- EDR Sensors: macOS-7.x and higher
- Workspace ONE UEM: 22.4.x.x
Resolution
1. Confirm the devices are registered.
2. Confirm the macOS devices are in the correct Smart Group.
3. Add all 3 required profiles documented in "Granting macOS Sensor Access on macOS 11.0+ Big Sur" into 1 policy:
a. Add a policy.
In the Workspace ONE UEM console (WS1), select Resources > Profiles & Baselines > Profiles > Add > Add Profile.
Select macOS. Select Device Profile.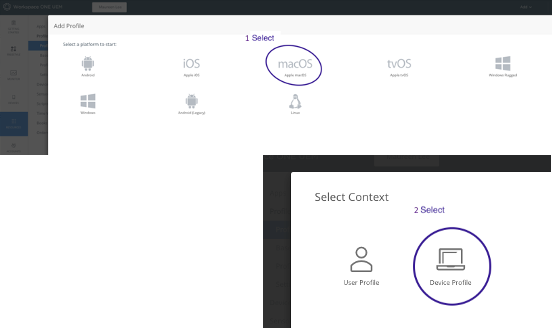
b. Fill in the General Section.
Name: VMware Carbon Black Profiles
Description: Contains SysExt Content and Full Disk
Deployment: Managed
Assignment Type: Auto
Allow Removal: Always
Managed By: <your account>
Smart Groups: <select a smart group with macos 11.x and 12.x devices>
Exclusions: NO
Additional Assignment Criteria: Do NOT select. 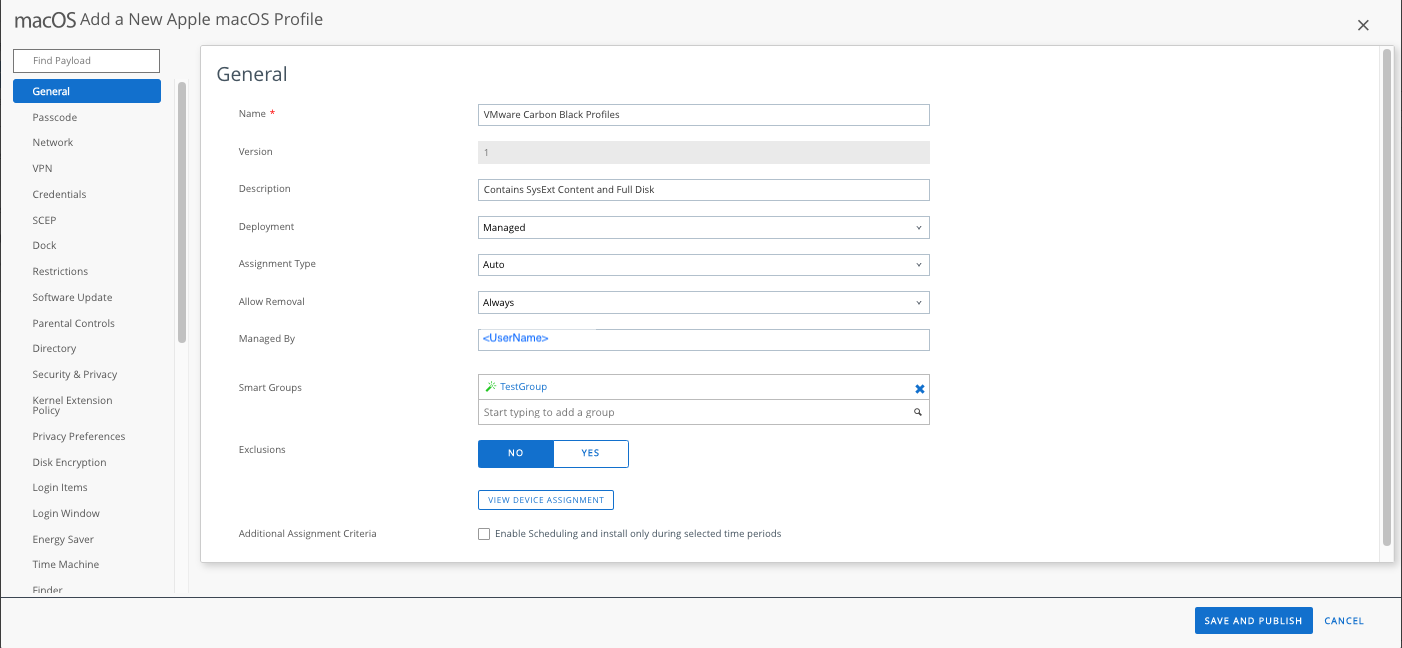 c. In the left margin, select System Extensions to add the CB System Extension policy.
c. In the left margin, select System Extensions to add the CB System Extension policy.
Hit the Configure button.
Allow User Overrides: Click to select.
Team Identifier: <leave the default>
Allowed System Extensions > Add System Extension.
Team Identifier: 7AGZNQ2S2T
Bundle Identifier: com.carbonblack.es-loader.es-extension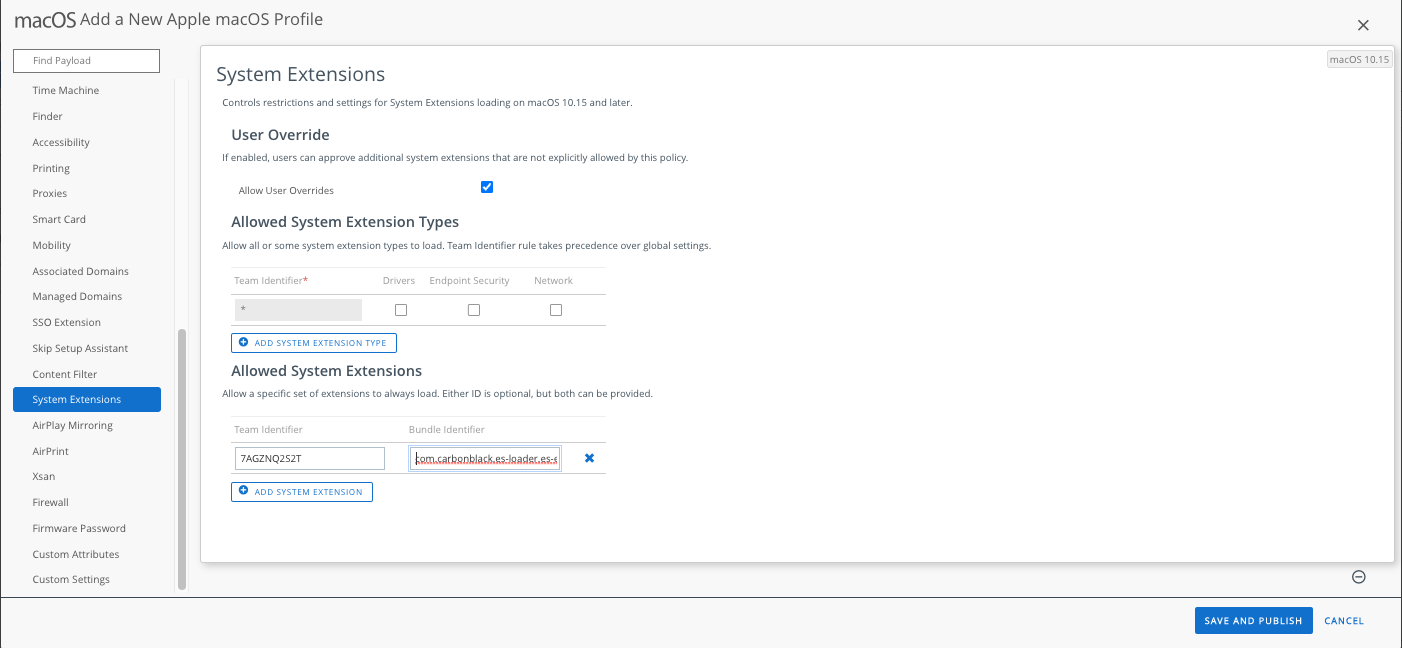
d. In the left margin, select Content Filter to add the CB Network Web Content policy.
Select CONFIGURE. (Note: The contents should be manually typed; Cut-n-Paste introduces hidden characters)
Filter Type: Plug-In
Filter Name: Carbon Black Network Content Filter
Identifier: com.carbonblack.es-loader
Service Address: <leave blank>
Organization: <leave blank>
Filter WebKit Traffic: Click to select.
Filter Socket Traffic: Click to select.
Authentication:
Username: <leave blank>
Password: <leave blank>
Identity Certificate: <leave blank>
Custom Data:
Select Add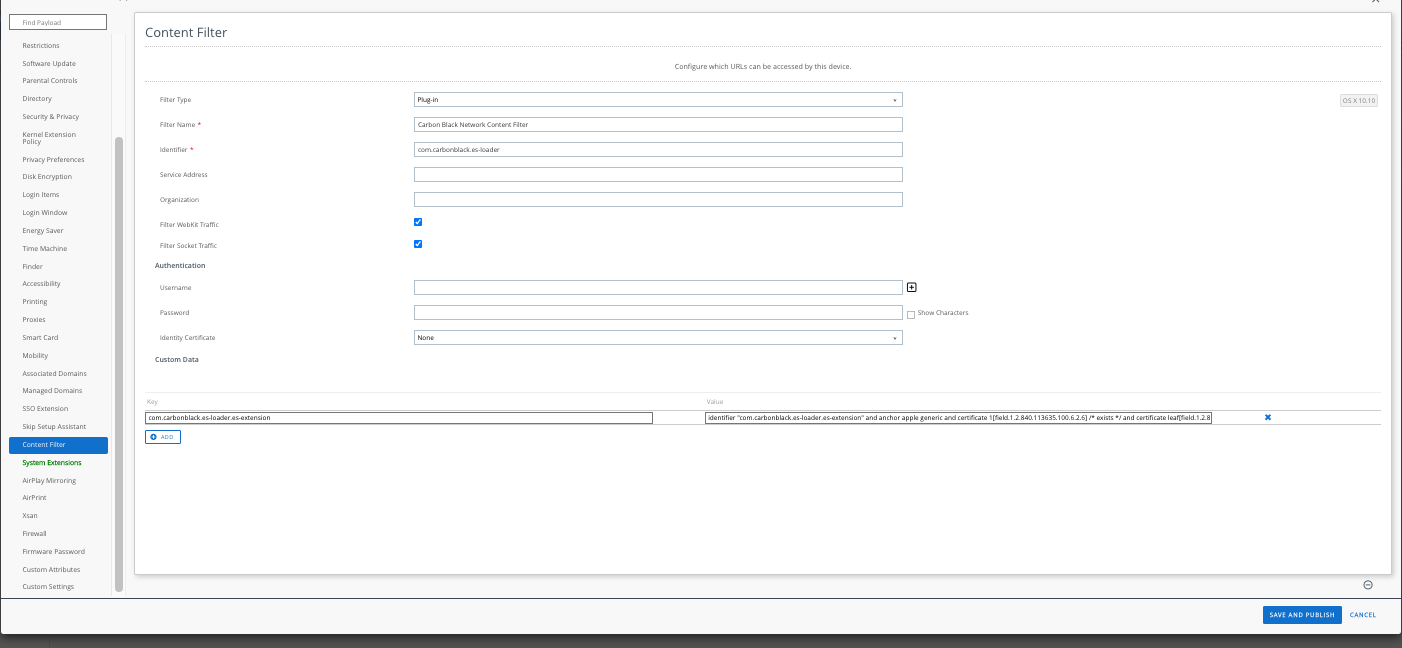
e. In the left margin, select Privacy Preferences to add the CB Privacy Profile.
Select CONFIGURE. (Note: The contents should be manually typed; Cut-n-Paste introduces hidden characters)
Select ADD APP.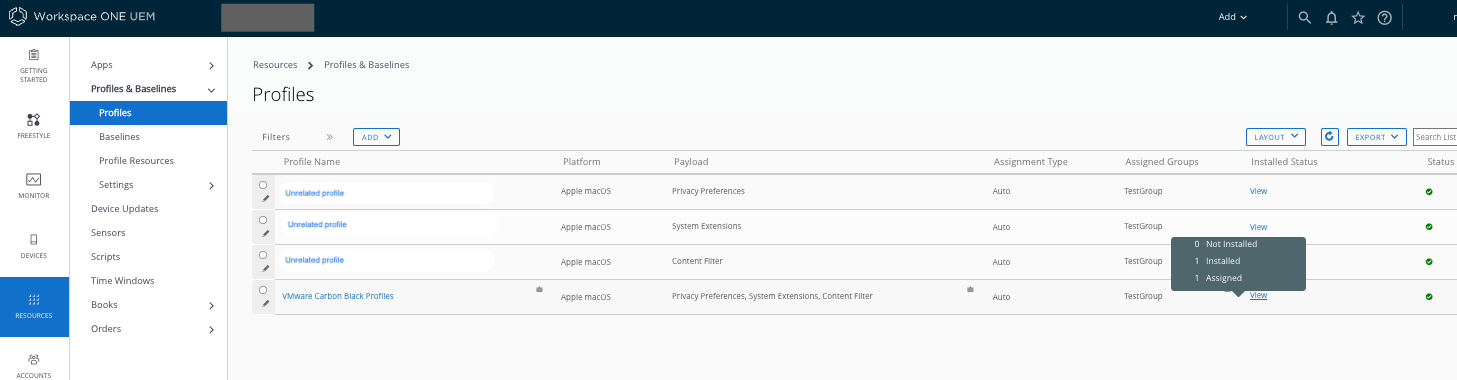
The policy has been created, saved and pushed to the devices. They reside on the sensor in /Library/Application\ Support/Airwatch/Data/profiles.plist.
The endpoint is ready for the VMware CB macOS 7.x install package.
2. Confirm the macOS devices are in the correct Smart Group.
3. Add all 3 required profiles documented in "Granting macOS Sensor Access on macOS 11.0+ Big Sur" into 1 policy:
a. Add a policy.
In the Workspace ONE UEM console (WS1), select Resources > Profiles & Baselines > Profiles > Add > Add Profile.
Select macOS. Select Device Profile.
Name: VMware Carbon Black Profiles
Description: Contains SysExt Content and Full Disk
Deployment: Managed
Assignment Type: Auto
Allow Removal: Always
Managed By: <your account>
Smart Groups: <select a smart group with macos 11.x and 12.x devices>
Exclusions: NO
Additional Assignment Criteria: Do NOT select.
Hit the Configure button.
Allow User Overrides: Click to select.
Team Identifier: <leave the default>
Allowed System Extensions > Add System Extension.
Team Identifier: 7AGZNQ2S2T
Bundle Identifier: com.carbonblack.es-loader.es-extension
d. In the left margin, select Content Filter to add the CB Network Web Content policy.
Select CONFIGURE. (Note: The contents should be manually typed; Cut-n-Paste introduces hidden characters)
Filter Type: Plug-In
Filter Name: Carbon Black Network Content Filter
Identifier: com.carbonblack.es-loader
Service Address: <leave blank>
Organization: <leave blank>
Filter WebKit Traffic: Click to select.
Filter Socket Traffic: Click to select.
Authentication:
Username: <leave blank>
Password: <leave blank>
Identity Certificate: <leave blank>
Custom Data:
Select Add
Key: com.carbonblack.es-loader.es-extension
Value: identifier "com.carbonblack.es-loader.es-extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
Value: identifier "com.carbonblack.es-loader.es-extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
Select CONFIGURE. (Note: The contents should be manually typed; Cut-n-Paste introduces hidden characters)
Select ADD APP.
Identifier: com.carbonblack.CbOsxSensorService
Identifier Type: Bundle ID
Code Requirement: identifier "com.carbonblack.CbOsxSensorService" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
Static Code: <do not select>
Comment: <leave blank>
Services:
Identifier Type: Bundle ID
Code Requirement: identifier "com.carbonblack.CbOsxSensorService" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
Static Code: <do not select>
Comment: <leave blank>
Services:
Address Book: <leave blank>
...
Find System Policy All Files Select Allow
... Leave all other options blank.
...
Find System Policy All Files Select Allow
... Leave all other options blank.
Select Save
Select ADD APP
Example of one app:
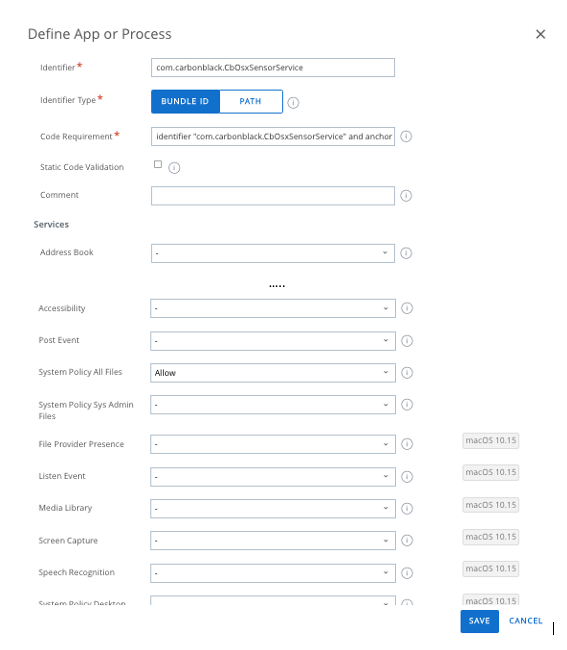
Select ADD APP
Identifier: com.carbonblack.es-loader.es-extension
Identifier Type: Bundle ID
Code Requirement: identifier "com.carbonblack.es-loader.es-extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
Static Code: <do not select>
Comment: <leave blank>
Services:
Identifier Type: Bundle ID
Code Requirement: identifier "com.carbonblack.es-loader.es-extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
Static Code: <do not select>
Comment: <leave blank>
Services:
Address Book: <leave blank>
...
Find System Policy All Files Select Allow
... Leave all other options blank.
...
Find System Policy All Files Select Allow
... Leave all other options blank.
Select Save
Example of one app:
f. Select Save and Publish
g. Select Publish
h. Confirm from WS1 console that the new policy has been pushed to the devices in the smart group. Click 'View' of the Profile created and a pop-up reports the profile is Installed and Assigned.
g. Select Publish
h. Confirm from WS1 console that the new policy has been pushed to the devices in the smart group. Click 'View' of the Profile created and a pop-up reports the profile is Installed and Assigned.
The policy has been created, saved and pushed to the devices. They reside on the sensor in /Library/Application\ Support/Airwatch/Data/profiles.plist.
Additional Information
- It is best to test the policy on 1-2 sensors prior to a large deployment to confirm the policies work. Confirm filemods, modloads and netconns are reporting to the EDR console.
- Confirm a complete install using the following commands on the endpoint:
cat /var/log/cblog.log (Good: activating extension success and Launching daemon) systemextensionsctl list (Good: Only one Cb extension which is active, enabled) log show -start "yyyy-mm-dd xx:xx:xx" --debug | grep -i cbosx [where xx is the time of installation] (Good: Look for event types 1, 2 and 5 followed by data)
- Troubleshooting Tips:
- If filemods and modloads are not reporting into the EDR console, then review the Privacy Preferences section for errors.
- If netconns are not reporting into the EDR console, then review the Content Filter for errors.
- The contents should be manually typed; Cut-n-Paste introduces hidden characters and the policy fails.
- Export the policy xml; On a Mac or Linux OS use less <xml> to identify extra characters. If needed use 'hexdump -C <xml>' and compare to a working policy xml provided by Support.
- If the policy needs to be corrected, it is best to uninstall, reboot, confirm the correct policy is installed and use the silent installer to install again.
launchctl unload /Library/LaunchDaemons/com.carbonblack.daemon.plist /Applications/"VMware Carbon Black EDR.app"/Contents/Resources/sensoruninst.sh reboot & check new policy installer -pkg /dirtopkg/CarbonBlackClientSetup.pkg -target /
- WS1 importing of a profile defaults to a iOS profile instead of macOS, therefore as of Mar 2022 an exported macOS XML can not be properly imported into WS1.
Feedback
Yes
No
