The CA PAM Agent is unable to connect to a CA PAM server
Article ID: 191526
Updated On:
Products
CA Privileged Access Manager (PAM)
Issue/Introduction
Trying to connect to CA PAM via CA PAM Agent results in an error :
PAM-AGT-1002:Cannot connect to the PAM server.
This happens irrespective of whether FQDN or IP address of PAM server is used.
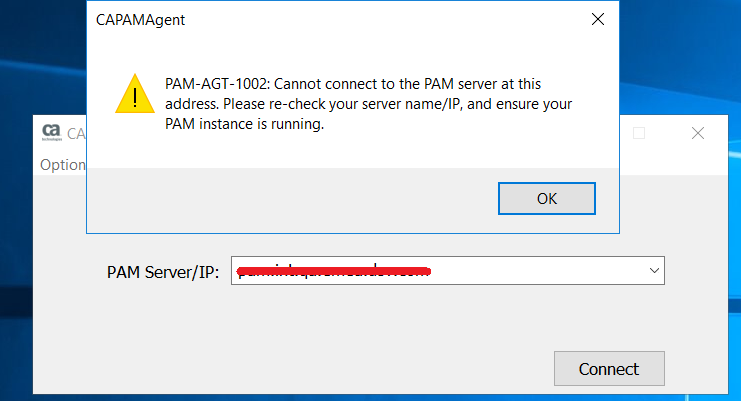
However the certificates from the different PAM nodes are fine
In the CA Agent Log files (under C:\Program Files\CA Technologies\CA PAM Agent\Logs), the CA PAM Client log, CAPAMAgent.log, shows errors like the following
[2020-05-20 08:34:34.772] [4272] [error] SslSocket_verify_callback() -> verify error=20, reason=[unable to get local issuer certificate], depth=0
[2020-05-20 08:34:34.773] [4272] [error] SslSocket_verify_callback() -> cert subject name=[/C=XX/ST=XXXXX/L=XXXXX/O=XXX A/S/OU=XXXX IT/CN=XXX.XXX.XXX]
[2020-05-20 08:34:34.773] [4272] [error] SslSocket::SslHandshake(), calling SSL_connect() with socket 636 failed, reason = [error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed]
[2020-05-20 08:34:34.773] [4272] [info] CertificateFileStore::GetDerEncodedCertDetails(), start getting certificate details from a DER encoded certificate
[2020-05-20 08:34:34.777] [4272] [info] CertificateFileStore::GetDerEncodedCertDetails(), finished getting certificate details from a DER encoded certificate
[2020-05-20 08:34:38.592] [4272] [info] CertificateFileStore::ImportDerEncodedCertificateToStore(), importing a DER encoded certificate to a certificate store in file [C:\Program Files\CA Technologies\CA PAM Agent\\Data\cacerts.sto] succeeded
[2020-05-20 08:34:38.625] [4272] [error] SslSocket_verify_callback() -> verify error=20, reason=[unable to get local issuer certificate], depth=0
[2020-05-20 08:34:38.625] [4272] [error] SslSocket_verify_callback() -> cert subject name=[C=XX/ST=XXXXX/L=XXXXX/O=XXX A/S/OU=XXXX IT/CN=XXX.XXX.XXX]
PAM-AGT-1002:Cannot connect to the PAM server.
This happens irrespective of whether FQDN or IP address of PAM server is used.
However the certificates from the different PAM nodes are fine
In the CA Agent Log files (under C:\Program Files\CA Technologies\CA PAM Agent\Logs), the CA PAM Client log, CAPAMAgent.log, shows errors like the following
[2020-05-20 08:34:34.772] [4272] [error] SslSocket_verify_callback() -> verify error=20, reason=[unable to get local issuer certificate], depth=0
[2020-05-20 08:34:34.773] [4272] [error] SslSocket_verify_callback() -> cert subject name=[/C=XX/ST=XXXXX/L=XXXXX/O=XXX A/S/OU=XXXX IT/CN=XXX.XXX.XXX]
[2020-05-20 08:34:34.773] [4272] [error] SslSocket::SslHandshake(), calling SSL_connect() with socket 636 failed, reason = [error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed]
[2020-05-20 08:34:34.773] [4272] [info] CertificateFileStore::GetDerEncodedCertDetails(), start getting certificate details from a DER encoded certificate
[2020-05-20 08:34:34.777] [4272] [info] CertificateFileStore::GetDerEncodedCertDetails(), finished getting certificate details from a DER encoded certificate
[2020-05-20 08:34:38.592] [4272] [info] CertificateFileStore::ImportDerEncodedCertificateToStore(), importing a DER encoded certificate to a certificate store in file [C:\Program Files\CA Technologies\CA PAM Agent\\Data\cacerts.sto] succeeded
[2020-05-20 08:34:38.625] [4272] [error] SslSocket_verify_callback() -> verify error=20, reason=[unable to get local issuer certificate], depth=0
[2020-05-20 08:34:38.625] [4272] [error] SslSocket_verify_callback() -> cert subject name=[C=XX/ST=XXXXX/L=XXXXX/O=XXX A/S/OU=XXXX IT/CN=XXX.XXX.XXX]
Environment
CA Privileged Access Management 3.2.X and above
Cause
This is a problem with the certificate. There are several underlying possible root causes for the problem
- Expired certificates for the appliances the CA Agent is connecting to
- Unable to verify the certificate upon connection due to CA certificates not being present in the CA PAM Agent certificate store
- In a cluster environment, the certificate does not contain in the Subject Alternate Names all the names that the cluster and its nodes may be responding as
Resolution
Please verify the following points
- If this is a cluster environment and the cluster certificate is issued by a third party authority make sure that the certificate Subject Alternate Names field contains the names and ip addresses of all the members of the cluster as well as the cluster external facing VIP name and IP address
- Check that the certificates presented by the cluster nodes are not expired
- Make sure that the whole chain of certification is loaded to the CA PAM Agent. That it, make sure that the root CA and intermediate CA which are the issuers of the certificate that CA PAM is using for connection are also in the CA PAM Agent certificate store. These certificates are easy to download by accessing PAM with a browser and clicking on the padlock/shield in the address bar (or whatever equivalent symbol you have, depending on your browser vendor), then exploring the intermediate and root certificate authorities therein, and exporting them to text file, from where they can be imported into CA PAM Agent (Go to Options --> Certificates and import them in that screen)
Feedback
Yes
No
