Creating a PAM user role with Global Admin rights and no permissions to View Passwords.
Article ID: 186880
Updated On:
Products
CA Privileged Access Manager (PAM)
Issue/Introduction
Is it possible to create a PAM role having 'Global Administrator' rights without 'Password View' permissions?
Environment
Product: Layer 7 Privileged Access Manager.
Version: 3.x
Version: 3.x
Resolution
These are the steps to create such a role:
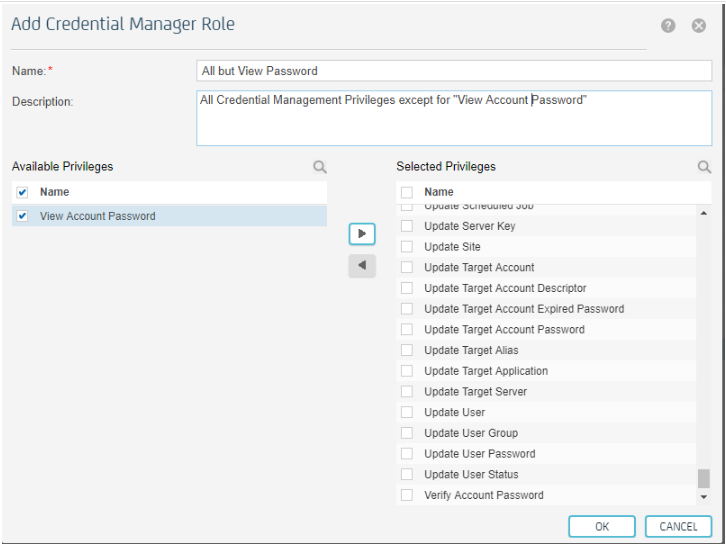
* Create a new Credential Manager Role "All but View Password" having all the privileges except for 'View Account Password':
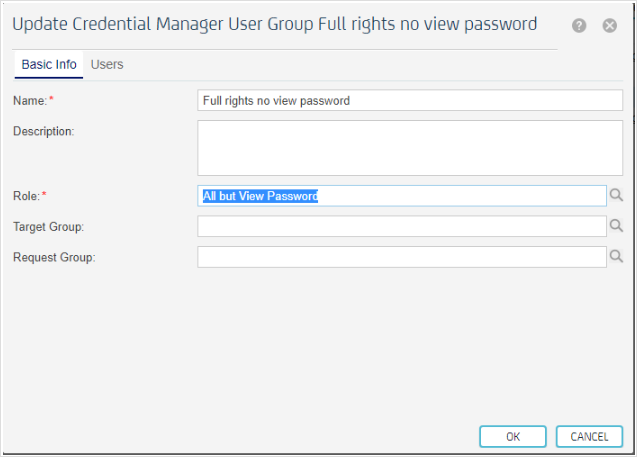
After that, create a Credential Manager User Group named "Full rights no view password" and assign it the "All but View Password" role previously created:
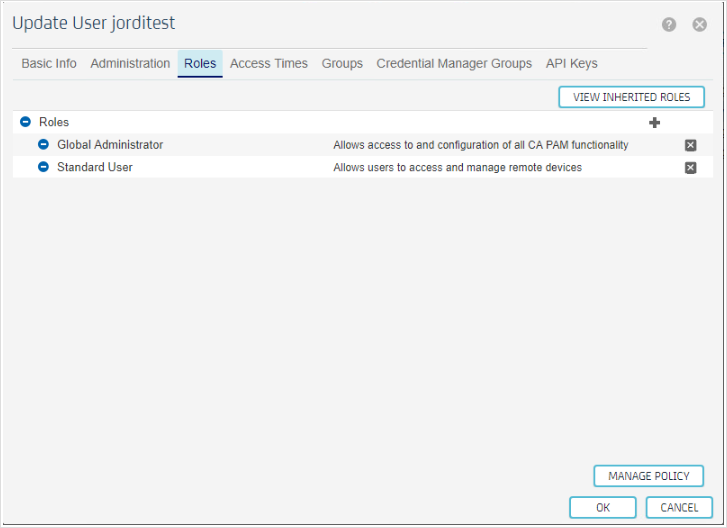
Afterwards, create a user 'jorditest' and in the user manager grant it with 'Global Administrator' role:
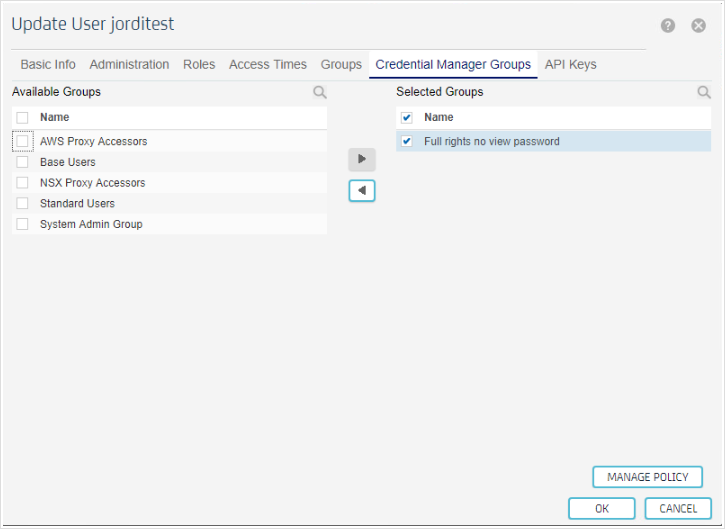
and in the "Credential Manager Group" tab assign it the 'Full rights no view password' group previously created:
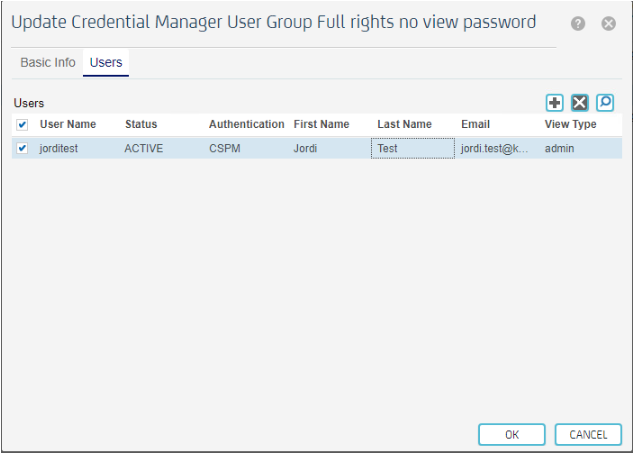
Going back to the Credential Manager User Group 'Full rights no view password' we can verify that the 'jorditest' user is there:
The main problem in this scenario is that the 'jorditest' user has no access to credential management in any way, so it cannot open a RDP or SSH session to any device because it cannot retrieve the password from the credential management database.
PAM is internally composed by two different sub-applications: Access Management and Credential Management.
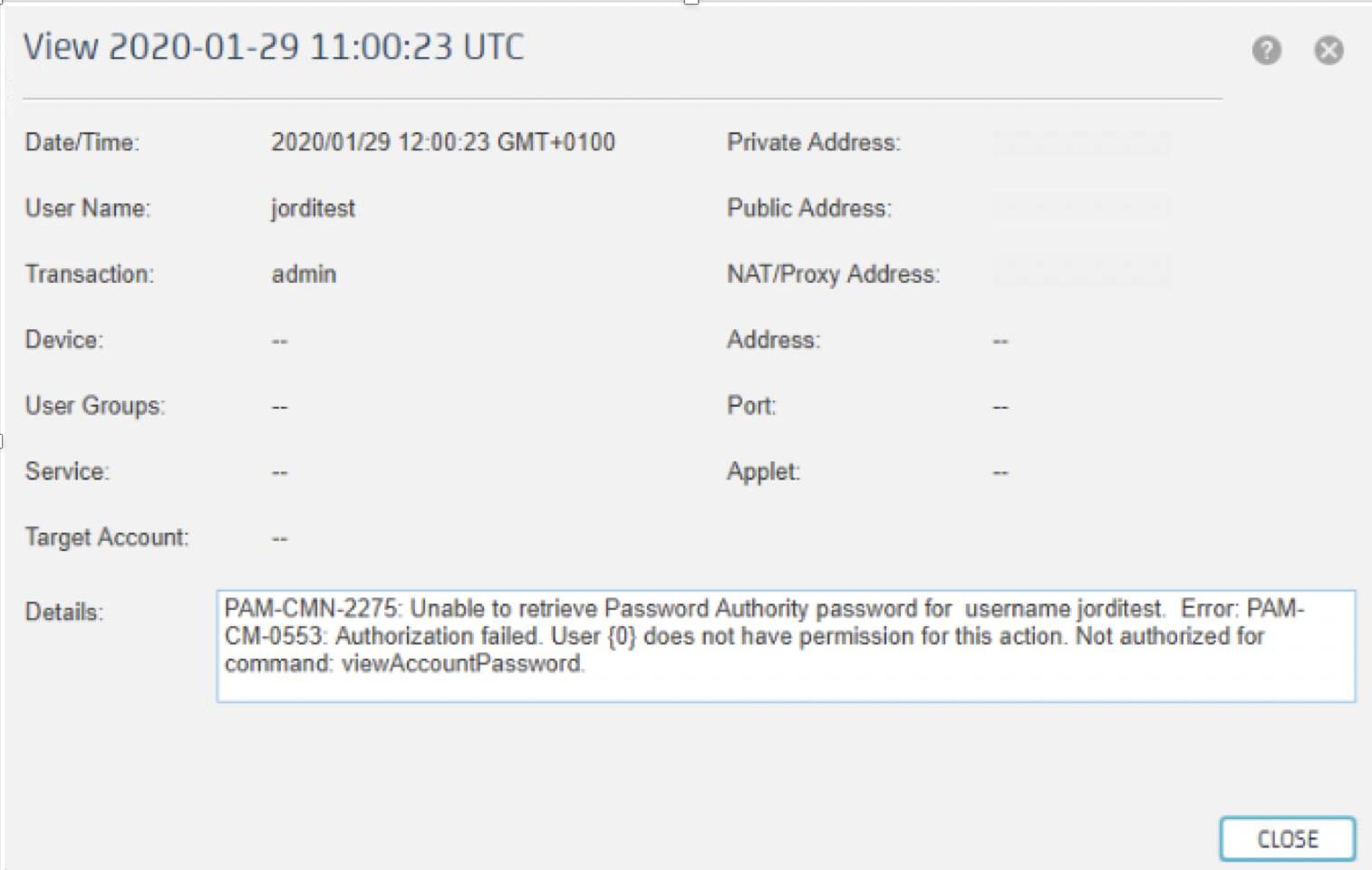
By design, Access Management acts as a client of Credential Management at the moment any interaction with credentials should be done. As 'jorditest' cannot View Passwords, the credential information to open the session is not available as per this policy. This is shown in the session logs when an access to a device with password injection is performed:
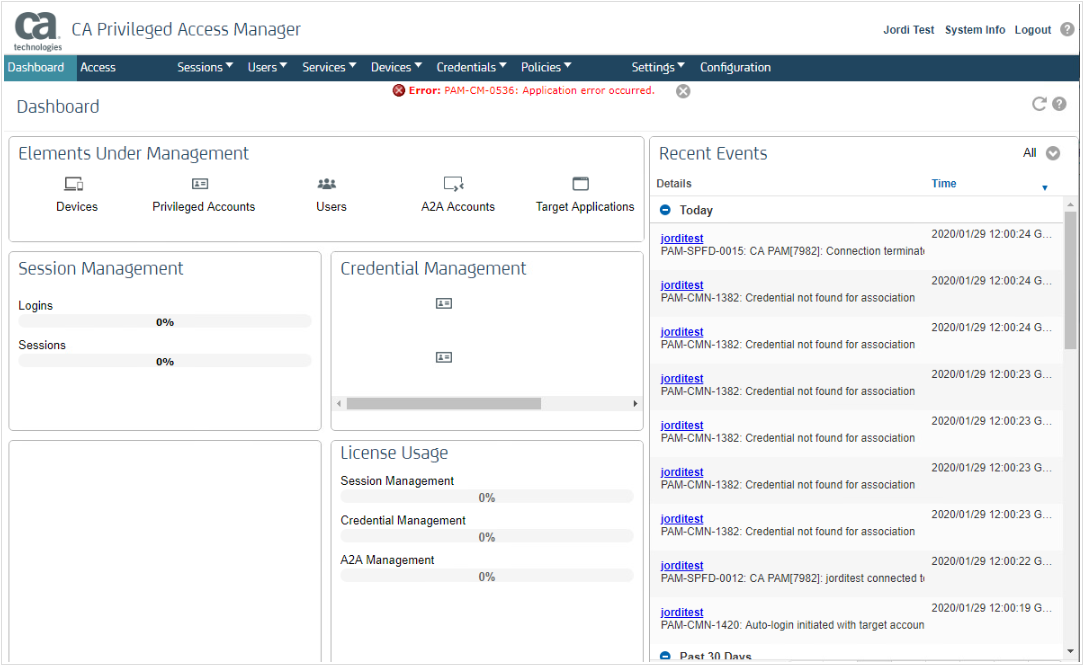
This is also impacting the main Dashboard with errors as it checks information from the Credential Management:
So, apparently, it seems not a good idea having a user with a combination of these roles: 'Global Administrator' (from Access Management) and 'Full rights no view password' (from Credential Management).
* Create a new Credential Manager Role "All but View Password" having all the privileges except for 'View Account Password':
After that, create a Credential Manager User Group named "Full rights no view password" and assign it the "All but View Password" role previously created:
Afterwards, create a user 'jorditest' and in the user manager grant it with 'Global Administrator' role:
and in the "Credential Manager Group" tab assign it the 'Full rights no view password' group previously created:
Going back to the Credential Manager User Group 'Full rights no view password' we can verify that the 'jorditest' user is there:
The main problem in this scenario is that the 'jorditest' user has no access to credential management in any way, so it cannot open a RDP or SSH session to any device because it cannot retrieve the password from the credential management database.
PAM is internally composed by two different sub-applications: Access Management and Credential Management.
By design, Access Management acts as a client of Credential Management at the moment any interaction with credentials should be done. As 'jorditest' cannot View Passwords, the credential information to open the session is not available as per this policy. This is shown in the session logs when an access to a device with password injection is performed:
This is also impacting the main Dashboard with errors as it checks information from the Credential Management:
So, apparently, it seems not a good idea having a user with a combination of these roles: 'Global Administrator' (from Access Management) and 'Full rights no view password' (from Credential Management).
Feedback
Yes
No
