Is CABI Jaspersoft vulnerable by CVE-2020-1938 "GhostCat" vulnerability?
Article ID: 185860
Updated On:
Products
Spectrum
ServiceDesk
Server Management Suite
Clarity PPM On Premise
Network Observability
Issue/Introduction
Is CABI Jaspersoft vulnerable by CVE-2020-1938 "GhostCat" vulnerability?
Environment
All CABI Jaspersoft Versions
Cause
Out of the box, CABI Jaspersoft is vulnerable by this GhostCat vulnerability.
However, this is only due to TIBCO leaving the connector on - though it is not used by Broadcom products.
Resolution
The AJP Connector can be commented out / removed from the server.xml file for CABI Jaspersoft without affecting the product and it's integration with Broadcom Products.
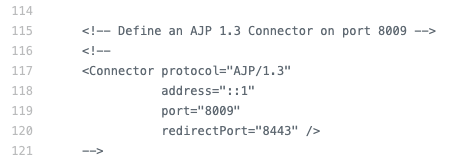
.....
simply comment out the AJP connector from the */conf/server.xml file:
.....
windows default path:: C:\Program Files\CA\SC\CA Business Intelligence\apache-tomcat\conf\server.xml
<?xml version="1.0" encoding="UTF-8" standalone="no"?><Server port="8005" shutdown="SHUTDOWN">
<Listener className="org.apache.catalina.startup.VersionLoggerListener"/>
<Listener SSLEngine="on" className="org.apache.catalina.core.AprLifecycleListener"/>
<Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener"/>
<Listener className="org.apache.catalina.mbeans.GlobalResourcesLifecycleListener"/>
<Listener className="org.apache.catalina.core.ThreadLocalLeakPreventionListener"/>
<GlobalNamingResources>
<Resource auth="Container" description="User database that can be updated and saved" factory="org.apache.catalina.users.MemoryUserDatabaseFactory" name="UserDatabase" pathname="conf/tomcat-users.xml" type="org.apache.catalina.UserDatabase"/>
</GlobalNamingResources>
<Service name="Catalina">
<Connector URIEncoding="UTF-8" connectionTimeout="20000" port="8080" protocol="HTTP/1.1" redirectPort="8443"/>
<!--
<Connector port="8009" protocol="AJP/1.3" redirectPort="8443"/>
-->
<Engine defaultHost="localhost" name="Catalina">
<Realm className="org.apache.catalina.realm.LockOutRealm">
<Realm className="org.apache.catalina.realm.UserDatabaseRealm" resourceName="UserDatabase"/>
</Realm>
<Host appBase="webapps" autoDeploy="true" name="localhost" startStopThreads="-1" unpackWARs="true">
<Valve className="org.apache.catalina.valves.AccessLogValve" directory="logs" pattern="%h %l %u %t "%r" %s %b" prefix="localhost_access_log" suffix=".txt"/>
</Host>
</Engine>
</Service>
</Server>..
Additional Information
Note: CABI 7.9.1 ships with Apache Tomcat/8.5.64 which is not vulnerable
Feedback
Yes
No
