Cannot access SSL sites using TLSv1.3
Article ID: 185069
Updated On:
Products
Issue/Introduction
Symantec was alerted to an interoperability issue between ProxySG and ASG products and TLS 1.3 in certain configurations. Google recently enabled field trial support for TLS 1.3, in Chrome Browser and ChromeOS 56 while accessing select Google servers.
Users of Symantec ProxySG, other proxy and filtering solutions may see a connection issue as a result. Clients that enable TLS 1.3, (Chrome 56 and later versions, FireFox 52 and later versions) and access TLS 1.3 enabled servers, may experience SSL connection failures when going through ProxySG or ASG.
Environment
- ProxySG 6.5.9.x or earlier releases
- ASG 6.6.5.3 or earlier releases
- ProxySG 6.6.5.3 or earlier releases
- ProxySG 6.7.1.1
Resolution
Fixes for TLS 1.3 interoperability are included in the following releases. Symantec recommends that you upgrade to these or later releases to avoid the issue.
- SG 6.5.10.4 - May 16, 2017
- SG 6.6.5.9 - May 24, 2017
- ASG 6.6.5.9 - May 24, 2017
- SG 6.7.1.3 - May 26, 2017
- Cloud SWG (formerly known as WSS) - March 4, 2017
Workaround
Chrome
TLS 1.3 can be disabled by accessing URL “chrome://flags/#tls13-variant”, changing the setting from “Default” to “Disabled”, and then relaunching Chrome. The below image shows the configuration set to TLS 1.2:
Note: Chrome will use TLS 1.3 by default starting with Chrome version 65.
FireFox
TLS 1.3 can be disabled by accessing URL “about:config”, search for security.tls.version.max, change it from “4”, which is TLS 1.3, to “3”, which is TLS 1.2, and restart the browser. The below image shows the the configuration set to “3”, which is TLS 1.2:
How to confirm if TLS 1.3 is supported by a browser
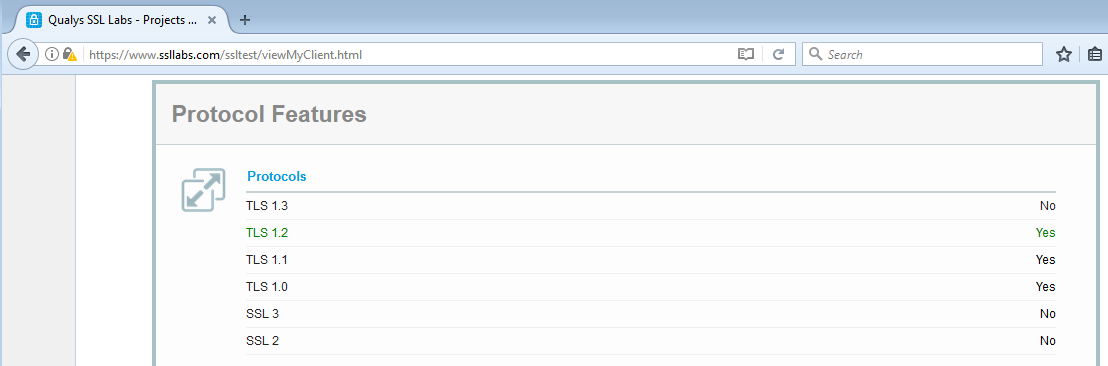
SSL Labs provides a URL which will test and report the TLS versions supported by the browser requesting the URL. That URL is https://www.ssllabs.com/ssltest/viewMyClient.html. The following screenshots show the results of the above URL on FireFox 52 with its default configuration:
And after following the steps above to disable TLS 1.3 support:
Workaround on ProxySG or ASG
For explicit deployments policy can be added to disable protocol detection for any impacted website. The following knowledge base article describes how this is done in policy: Disable Detect Protocol on exception to resolve an issue with SSL interception failure. For transparent deployments, a TCP-Tunnel service will need to be created that includes the affected destination IPs. The following knowledge base article describes how this is done in proxy services:
https://knowledge.broadcom.com/external/article?legacyId=TECH245661
Workaround in Cloud SWG
Cloud SWG supports TLS 1.3 since February 2022. The options to bypass TLS 1.3 sites still exists though:
- Cloud SWG Administrators can implement the ProxySG CPL change, assuming that Cloud SWG is managed using Management Center.
- In the scenario where Cloud SWG is managed via the Cloud SWG Portal, the destination IP address or domain must be manually added to the Malware and Scanning destination exemptions under Policy -> Malware and Scanning. Note that destinations domains must be added without any scheme i.e. using imply the domain name without any URL path or protocol (http/https)
